Thanks drome for sharing his knowledge and skills! He completed all 10 challenges and this series of writeups is done by him :)
| Details | Links |
|---|---|
| Official Challenge Site | https://flare-on.com/ |
| Official Challenge Announcement | https://www.fireeye.com/blog/threat-research/2021/08/announcing-the-eighth-annual-flare-on-challenge.html |
| Official Solutions | https://www.mandiant.com/resources/flare-on-8-challenge-solutions |
| Official Challenge Binaries | http://flare-on.com/files/Flare-On8_Challenges.zip |
03_antioch
To solve this challenge, you’ll need to …AAARGH
7-zip password:flare
Docker File System Extraction
After unzipping the given 7z file, we get a tar file called antioch.tar. In the tar file we have a bunch of folders titled with hashes and a manifest.json and repositories files
|
|
We have to run the following commands to extract the file system out of this image
|
|
After that we untar the file and find that it has the following structure
|
|
AntiochOS is an ELF file, so we put it into IDA and start analysis.
Analysis
In the start function, the program prints some version info, AntiochOS, version 1.32 (build 1975), then reads a command from the user and calls a function accordingly. The available commands are quit, help, approach, and consult. The first two functions are self explanatory, while the other two require closer reversing.
approach
The function for approach is in sub_401640, where it would ask for a name from the user, then calculate the CRC32 checksum of that name with a trailing newline (sub_401B50), then compare the name against an array of checksums at 0x402000. If it matches the checksum of one of the elements, it would ask for the user’s quest (this is ignored), then ask for a favorite color from the user, check the CRC32 checksum of the color (also with a trailing newline) against the array, and if it matches, it would return a number from the table between 1 and 30 inclusive.
The table is an array of 30 structs, which we name as the hash_struct. Each hash_struct has 3 DWORDs inside, representing the name checksum, color checksum, and corresponding number returned if successful.
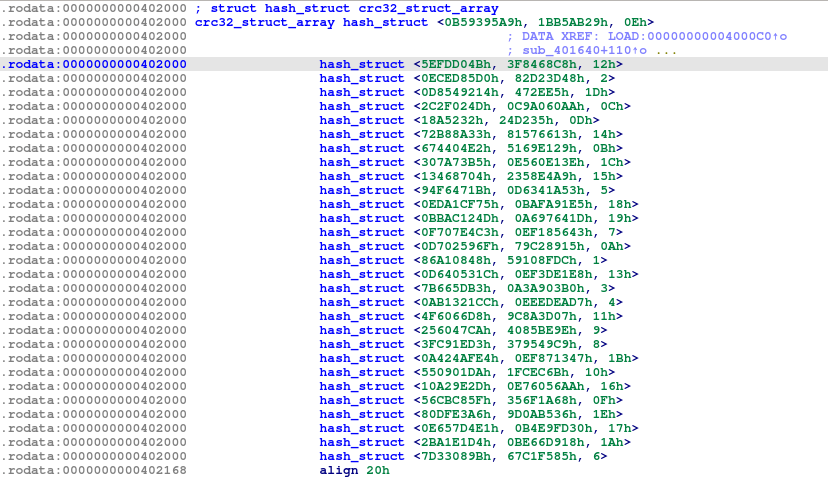
We checked the original Docker tar file, and found that there are 31 subdirectories inside, 30 of them containing layers with .dat files, and 1 containing the ELF file (7016b6). All the folders with the .dat files have author names in their json file which match the CRC32 values in the hash table, and we were able to match all 30 hash_structs to their author names.
To find the color names, we compiled all the colors from Wikipedia, and calculated their CRC32 checksums, but even then there were a few missing, namely 593028265, 3136983525, 4008569559, 3035233584, and 3194411288.
We saw more success when we used the wordlist from /usr/share/dict/words instead, which got us the colors of all 30 color CRC32 checksums, which looks like this:
[b'Bridge Keeper', b'Indigo', 14],
[b'Sir Lancelot', b'Blue', 18],
[b'Sir Bors', b'Coral', 2],
[b'Black Knight', b'Black', 29],
[b'Chicken of Bristol', b'Mint', 12],
[b'Roger the Shrubber', b'Tomato', 13],
[b'Rabbit of Caerbannog', b'Salmon', 20],
[b'Trojan Rabbit', b'Beige', 11],
[b'Dinky', b'Turquoise', 28],
[b'Sir Not-Appearing-in-this-Film', b'Transparent', 21],
[b'Brother Maynard', b'Crimson', 5],
[b'Inspector End Of Film', b'Gray', 24],
[b'Sir Ector', b'Bisque', 25],
[b'Sir Robin', b'Red', 7],
[b'Green Knight', b'Green', 10],
[b'Miss Islington', b'Brown', 1],
[b'Lady of the Lake', b'Gold', 19],
[b'Tim the Enchanter', b'Orange', 3],
[b'Dragon of Angnor', b'Khaki', 4],
[b'A Famous Historian', b'Pink', 17],
[b'Squire Concorde', b'Periwinkle', 9],
[b'Zoot', b'Tan', 8],
[b'Dennis the Peasant', b'Orchid', 27],
[b'Legendary Black Beast of Argh', b'Silver', 16],
[b'Prince Herbert', b'Wheat', 22],
[b'Sir Gawain', b'Azure', 15],
[b'Sir Gallahad', b'Yellow', 30],
[b'King Arthur', b'Purple', 23],
[b'Squire Patsy', b'Chartreuse', 26],
[b'Sir Bedevere', b'Teal', 6],
However, the approach function didn’t do anything else other than giving us the corresponding number, so we looked into the other function consult for more clues.
consult
The function for consult is in sub_401460. This function reads in all files from a.dat to z.dat, which are all 0x1000 bytes long, then xors their contents together, then use the result as indices in a character array at 0x404100 to generate some sort of ASCII art that is printed out.
We tried extracting the .dat files in one of the Docker layers, then placing the ELF file in the same folder and running consult, which prints out some string that looks like ASCII art but is unintelligible.
Back to Docker
The approach function clearly gives us some order of the layer folders according to their authors’ order numbers in the array, and the consult function suggests that we should get some ASCII art after retrieving and processing the correct .dat files. To find out how the layer folders are supposed to work together to produce the correct .dat files, we went to read up about how Docker image layers work.
Docker image layers (the 31 subdirectories in the tar file) are intermediate images used by Docker to cache intermediate stages so that it can rebuild images faster when small changes are made. The layers store the filesystem diffs made by the instructions in the Dockerfile, and the entire file is in each layer whenever there’s an add or change.
We initially tried to fix the saved docker image tar file to make it include the last layer, but found it very difficult as we didn’t understand how the docker save function works in depth.
Instead, we used the order of layers provided by the approach functions, and took the .dat file in the layer with a higher ordinal number as the more updated one, then used the processing method which we reversed from consult on all the updated .dat files, which gave us the flag in ASCII art.
Solution Script
|
|
which gives the following output:
...............
...............
...............
...............
...............
...............
...............
...............
...............
....______.....
...|..____|....
...|.|__.......
...|..__|......
...|.|.........
...|_|.........
...............
...............
...._..........
...(_).........
...._..........
...|.|.........
...|.|.........
...|_|.........
...............
...............
...............
...............
...__...__.....
...\.\././.....
....\.V./......
.....\_/.......
...............
...............
...............
...............
.....___.......
..../._.\......
...|..__/......
....\___|......
...............
...............
...............
...............
....______.....
...|______|....
...............
...............
...............
...............
...._____......
...|_..._|.....
.....|.|.......
.....|.|.......
...._|.|_......
...|_____|.....
...............
...............
...............
...............
....___........
.../.__|.......
...\__.\.......
...|___/.......
...............
...............
...............
...............
....______.....
...|______|....
...............
...............
...............
...............
...._____......
...|..__.\.....
...|.|__).|....
...|.._../.....
...|.|.\.\.....
...|_|..\_\....
...............
...............
...._..........
...(_).........
...._..........
...|.|.........
...|.|.........
...|_|.........
...............
...............
...............
...............
.....__._......
..../._`.|.....
...|.(_|.|.....
....\__,.|.....
.....__/.|.....
....|___/......
...._..........
...|.|.........
...|.|__.......
...|.'_.\......
...|.|.|.|.....
...|_|.|_|.....
...............
...............
...._..........
...|.|.........
...|.|_........
...|.__|.......
...|.|_........
....\__|.......
...............
...............
...............
...............
....______.....
...|______|....
...............
...............
...............
...............
.....____......
..../.__.\.....
...|.|..|.|....
...|.|..|.|....
...|.|__|.|....
....\____/.....
...............
...............
...............
...............
...._..._......
...|.|.|.|.....
...|.|_|.|.....
....\__,_|.....
...............
...............
...._..........
...|.|.........
...|.|_........
...|.__|.......
...|.|_........
....\__|.......
...............
...............
...............
......____.....
...../.__.\....
...././._`.|...
...|.|.(_|.|...
....\.\__,_|...
.....\____/....
...............
.....__........
..../._|.......
...|.|_........
...|.._|.......
...|.|.........
...|_|.........
...............
...............
...._..........
...|.|.........
...|.|.........
...|.|.........
...|.|.........
...|_|.........
...............
...............
...............
...............
.....__._......
..../._`.|.....
...|.(_|.|.....
....\__,_|.....
...............
...............
...............
...............
...._.__.......
...|.'__|......
...|.|.........
...|_|.........
...............
...............
...............
...............
.....___.......
..../._.\......
...|..__/......
....\___|......
...............
...............
...............
...............
....______.....
...|______|....
...............
...............
...............
...............
...............
...............
.....___.......
..../._.\......
...|.(_).|.....
....\___/......
...............
...............
...............
...............
...._.__.......
...|.'_.\......
...|.|.|.|.....
...|_|.|_|.....
...............
...............
...............
...............
...............
...............
...._..........
...(_).........
...............
...............
...............
...............
.....___.......
..../.__|......
...|.(__.......
....\___|......
...............
...............
...............
...............
.....___.......
..../._.\......
...|.(_).|.....
....\___/......
...............
...............
...............
...............
...._.__.___...
...|.'_.`._.\..
...|.|.|.|.|.|.
...|_|.|_|.|_|.
...............
...............
...............
...............
...............
...............
...............
...............
...............
Flag
Five-Is-Right-Out@flare-on.com