Thanks drome for sharing his knowledge and skills! He completed all 10 challenges and this series of writeups is done by him :)
| Details | Links |
|---|---|
| Official Challenge Site | https://flare-on.com/ |
| Official Challenge Announcement | https://www.fireeye.com/blog/threat-research/2021/08/announcing-the-eighth-annual-flare-on-challenge.html |
| Official Solutions | https://www.mandiant.com/resources/flare-on-8-challenge-solutions |
| Official Challenge Binaries | http://flare-on.com/files/Flare-On8_Challenges.zip |
04_myaquaticlife
What would Flare-On do without a healthy amount of nostalgia for the abraisive simplicity of 1990’s UI design? Probably do more actual work and less writing fun challenges like this.
7-zip password:flare
The 7z gives an executable file myaquaticlife.exe with the following properties:
arch x86
baddr 0x400000
binsz 2389687
bintype pe
bits 32
canary false
retguard false
class PE32
cmp.csum 0x00253d02
compiled Wed Nov 14 08:27:56 2007
crypto false
endian little
havecode true
hdr.csum 0x00000000
laddr 0x0
lang c
linenum true
lsyms true
machine i386
nx false
os windows
overlay true
cc cdecl
pic false
relocs true
signed false
sanitize false
static false
stripped false
subsys Windows GUI
va true
The file seems to be UPX packed, so we save a copy of the original executable and run:
upx -d myaquaticlife.exe
Looking at some of the strings inside like http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.c and Flash Player installation, it seems that it is a Shockwave Flash program packaged into an executable. However, we couldn’t find any tools that could extract the original script, so we just have to look at the executable.
The game looks like this when run:
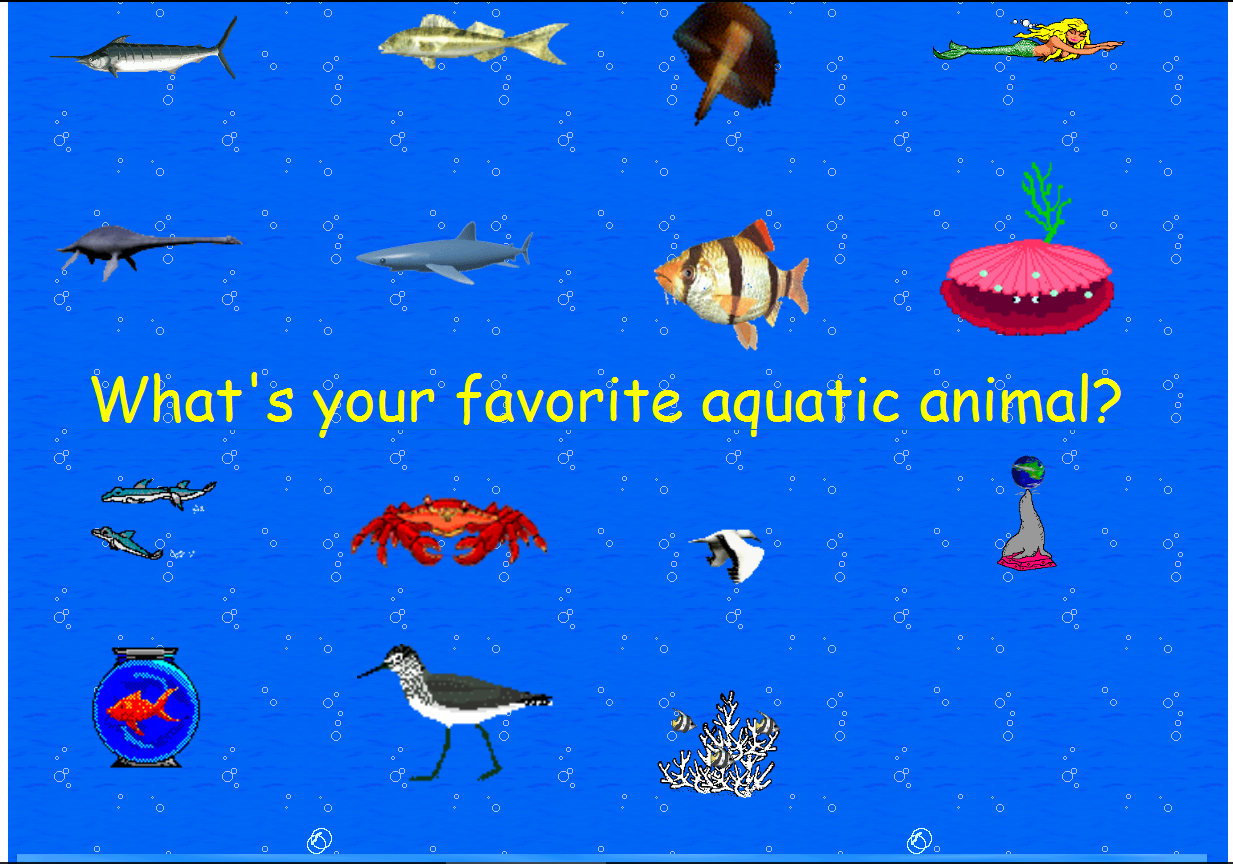
Every time we click on a fish, the following message appears on the IDA output
702C0000: loaded C:\Windows\SysWOW64\policymanager.dll
70250000: loaded C:\Windows\SysWOW64\msvcp110_win.dll
Unloaded C:\Windows\SysWOW64\msvcp110_win.dll
Unloaded C:\Windows\SysWOW64\policymanager.dll
The executable file is huge with many functions and has many C++ artifacts like virtual function tables that make it hard to analyze statically, so we debugged it in API Monitor to find any interesting API calls.
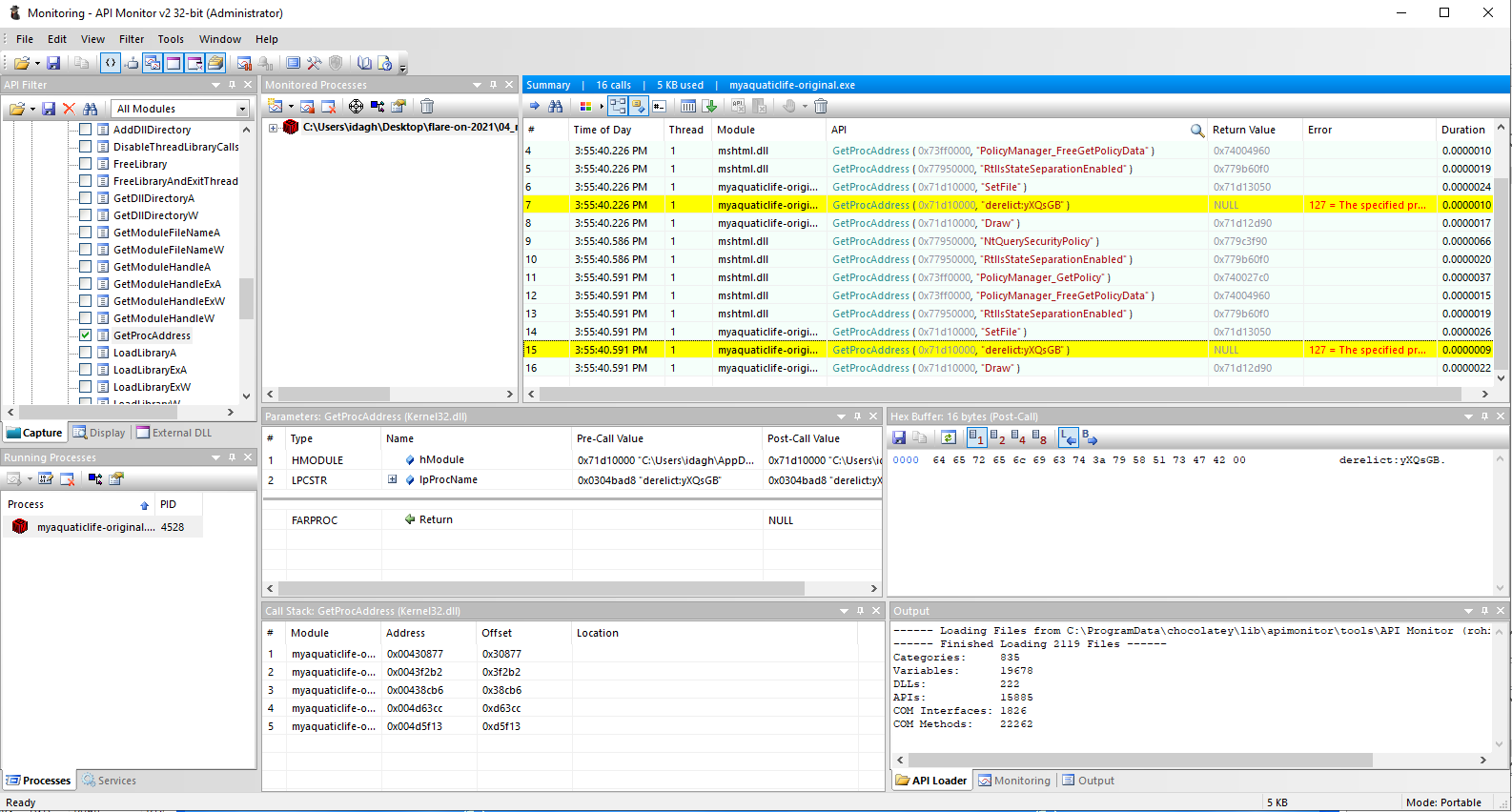
We find that every time we click a fish, the program would call GetProcAddress to get the address of SetFile and a (non-existent) function that looks something like flotsam:DFWEyEW or lagan:BAJkR, from the module at %temp%\MMBPlayer\fathom.dll.
We go to that folder at %temp%\MMBPlayer\, and find that other than that DLL, the program also drops the GIF files, and two HTML files that serve as the background.
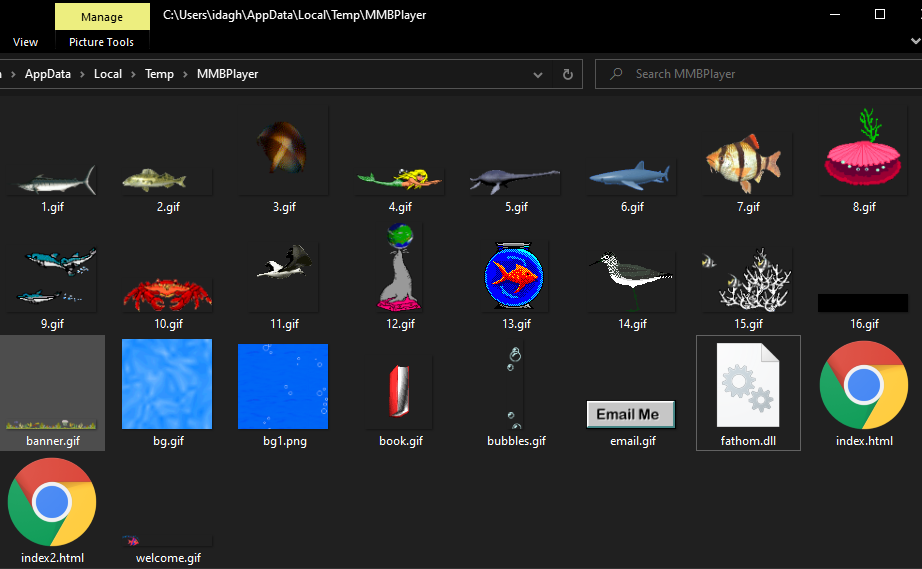
The index.html file renders the first page with all the fishes we see, and has the following code
|
|
The index2.html file renders the background page we get after clicking the center yellow text.
The text that gets sent for each fish clicked is as follows
1. derelict:MZZWP
2. lagan:BAJkR
3. flotsam:DFWEyEW
4. flotsam:PXopvM
5. derelict:LDNCVYU
6. derelict:yXQsGB
7. jetsam:newaui
8. lagan:QICMX
9. lagan:rOPFG
10.jetsam:HwdwAZ
11.jetsam:SLdkv
12.derelict:LSZvYSFHW
13.flotsam:BGgsuhn
14.derelict:LSZvYSFHW
15.derelict:RTYXAc
16.lagan:GTXI
We analyze the DLL and find that clicking on the center yellow text calls the PluginFunc19 export, and inside there is this code segment that looks suspicious
|
|
Here, v1 is a string that contains all the flotsam texts after the colons concatenated together, so for example pressing fish 3 then fish 4 would result in it being DFWEyEWPXopvM, while v13[0] is the same thing but for the jetsam fish. v16 is some encrypted text.
After that it calculates the MD5 hash of the processed text then compares it against 6c5215b12a10e936f8de1e42083ba184, so we write a script to try the different permutations of the concatenated strings that form v1 and v13.
|
|
This outputs b'PXopvMDFWEyEWBGgsuhn' b'SLdkvnewauiHwdwAZ'. This corresponds to fishes 4, 3, then 13 for flotsam, and fishes 11, 7, then 10 for jetsam.
We click the fishes in that order, and get the following screen:
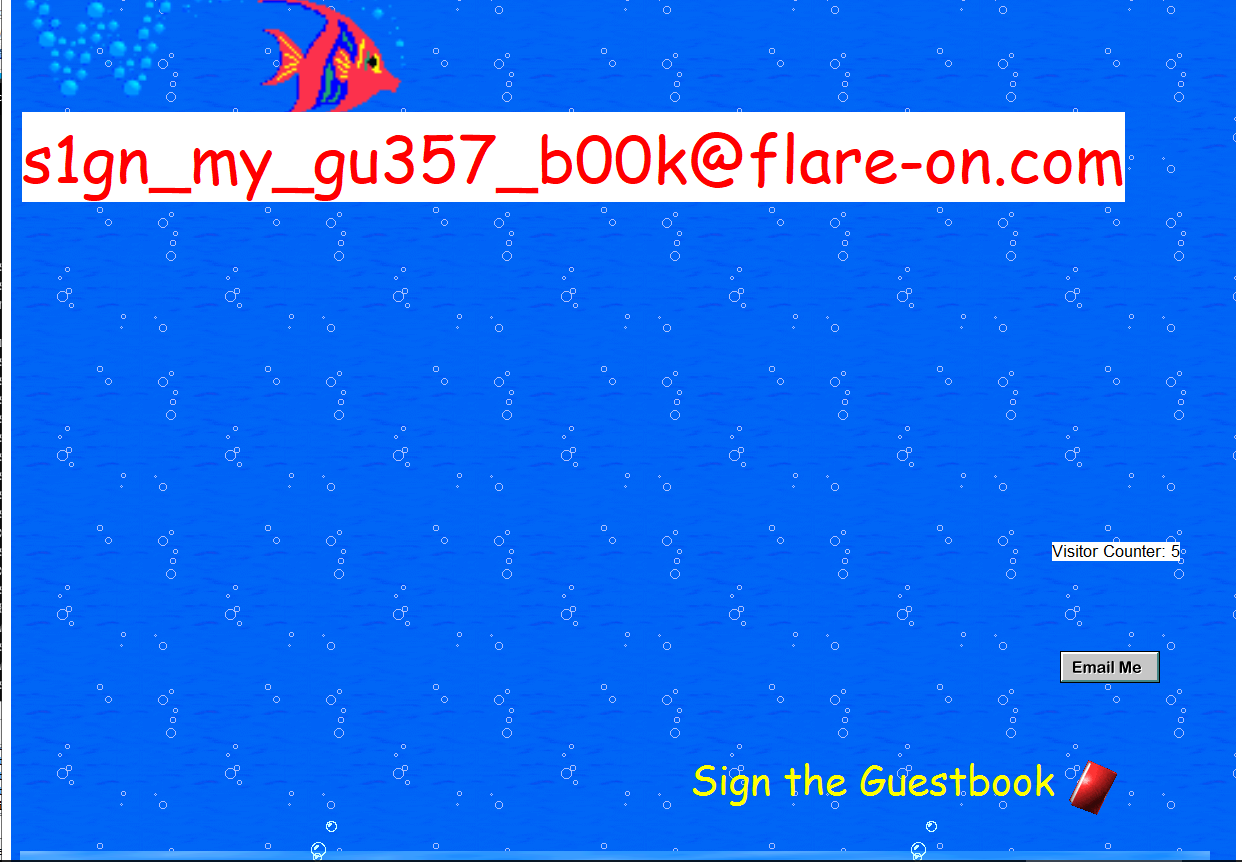
Flag
s1gn_my_gu357_b00k@flare-on.com