I joined the Junior Category this year and I’ll be frank: this was quite badly organized. It seems that they did not conduct any proper dry runs of the event. They had broken challenges (missing crucial challenge information, missing code in files, non-functional websites) and the worst thing is that they do not even announce when they are aware of the problem, when they are working on rectifying it, and when they have fixed it. Instead, we were left to figure out ourselves that a particular challenge file had been silently changed, or a vital piece of information was quietly added into some challenge description.
There were also insufficent challenges (or they were of inadequate difficulty) to cover the duration of the event, which rendered their plan and timing of staggered challenge releases meaningless. Many hours before each challenge-release checkpoint, the top teams were already tied by their scores and idling. This means that the final winner would essentially be based only on the last challenge-release – which was a Web mission comprising 3 challenges. But because the final Web challenge was inoperative, the top teams basically came to a tie again while waiting for the challenge to be fixed after solving the other 2. Initially, no one knew it was broken so we did not even know what payloads we sent were supposed to work. And when they said it was supposedly fixed, it wasn’t. Isn’t that disorienting?
Some more side points to note is that they delayed the winners announcement livestream 3 times for a total of 6 hours, and the live scoreboard was alphabetically sorted rather than based on time in the event that scores were tied.
Honestly, what’s even scarier is that I heard the Senior Category had even more serious issues, such as being only able to login a day after the competition started…
Anyway, big shoutout to my team for trying their best to find time to work on this together! We came in 3rd and that’s satisfactory.
🎵 Haywood - Backbeat was a really good tune that I put on for this CTF :)
Let’s Go Hunting (OSINT)
1. In Front of You
A new startup company called UnbreakableMailSystems develops a cutting-edge security product to prevent modern phishing attacks. They claim that their new product NoMorePhishing-ZX1 can prevent the Global Domination Corporation phishing campaign. Can we trust this product?
Searching for the company in Google brings us to a website unbreakablemailsystems.xyz where the flag is contained in the <meta> tag.
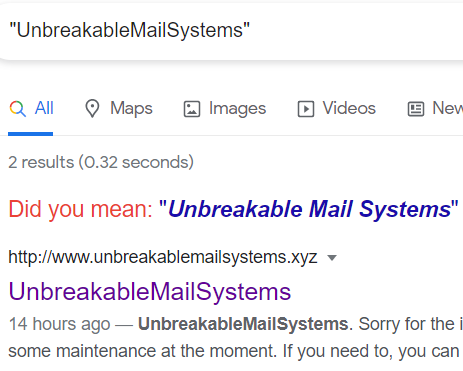
Flag:
CDDC21{It_was_an_Easy1}
2. Time Travel
One of our team members recommended the new NextCloudSecurity product CLOUDSEC2000TX. I tried to find some information about this product, but I couldn’t find anything. I think some of us are starting to lose it.
Google searching the company name gives us a website again at nextcloudsecurity.xyz except there is no flag.
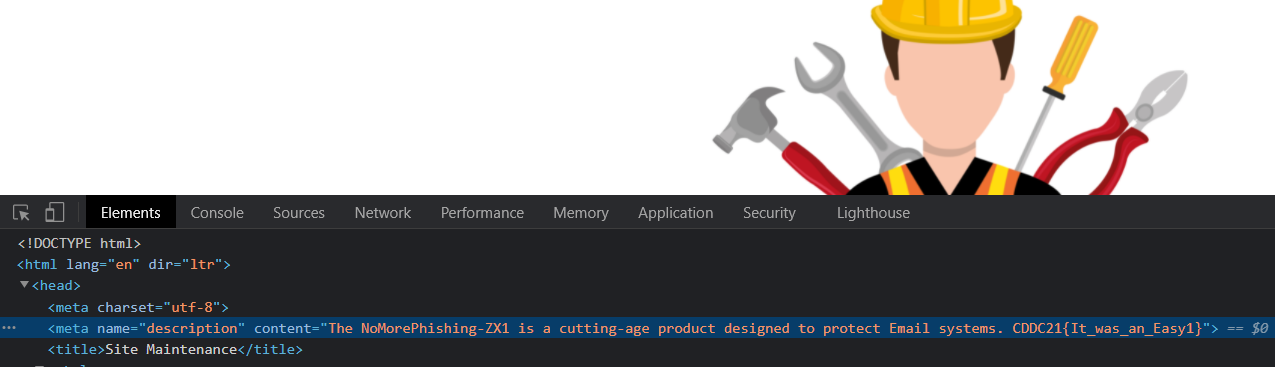
Since the challenge’s title was Time Travel, I thought to check for old archived snapshots of the site using the Wayback Machine. There was one capture with the link to the flag embedded as a HTML comment.
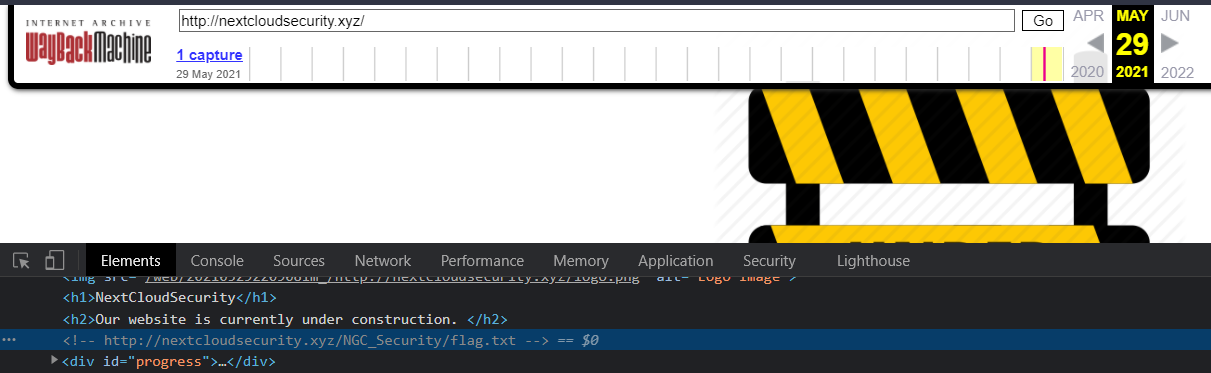
Visiting nextcloudsecurity.xyz/NGC_Security/flag.txt gives us the flag.
Flag: CDDC21{_T!me_TraveL_!s_REAl_}
3. Who is GDC?
The GlobalDominationCorporation, also known as GDC, uses several domains for their hostile activities. We only know about one of them; globaldominationcorporation.com. Unfortunately, we can’t provide you with more information. Can you try to gather some more information about them?
This challenge is pretty much the same as one in 2019’s CDDC qualifiers. I’m surprised they reused this considering the solution is unintuitive and somewhat unrealistic in terms of actual OSINT/reconnaissance methodology.
As hinted by the challenge title, run whois on the given domain with -H to omit the unnecessary legal disclaimers in return for more information.
|
|
Output:
|
|
Emailing the registrant gets us an auto-reply with the flag.
Flag: CDDC21{We_are_TheGl0bal_DOminat!on_Corporation!}
4. Name System
It’s unbelievable! Every day, we get a new piece of information about the Global Domination Corporation. Now it’s a new domain, globdominationcorp.com. I tried to check if they have a website at www[.]globdominationcorp.com, but there is nothing there. What else can we do?
I ran Sublist3r https://github.com/aboul3la/Sublist3r which is a very nice tool to enumerate and bruteforce subdomains.
|
|
Output:
|
|
Visiting internal.globdominationcorp.com gives us the flag.
Flag: CDDC21{EnumeRation_!s_the_KEY_F0R_EveryTHING!}
5. Broken System
The CryptIT Banking and Consulting company suspects that the GlobalDominationCorporation is attacking its email systems. They need your help to fix the misconfiguration.
Googling for “CryptIT Banking” points us to the website at cryptit.biz which does not contain anything interesting.
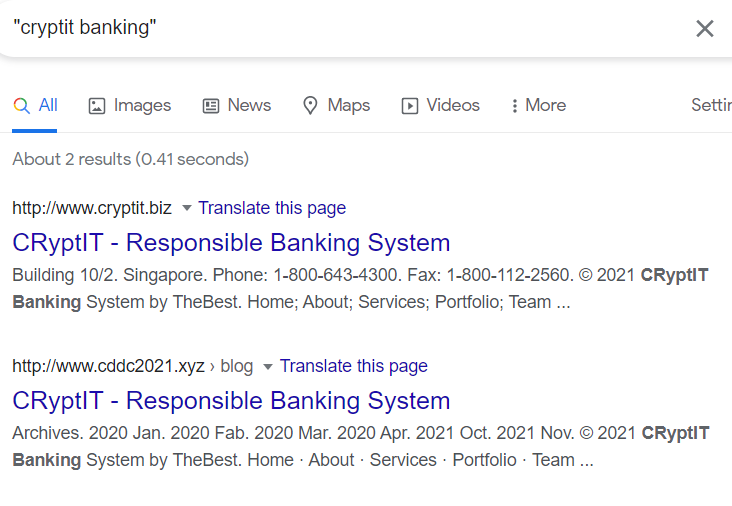
What did the description mean by “email system misconfigurations”? I googled that and it refreshed my mind that this could be related to SPF/DMARC/DKIM.
While we could dig each individual relevant subdomain like _spf.cryptit.biz to inspect each record as described here https://book.hacktricks.xyz/pentesting/pentesting-smtp#mail-spoofing, I found checkdmarc to be a very useful tool to just retrieve all records for us.
|
|
Output:
|
|
The flag turned out to be stored in the TXT record of the _dmarc.cryptit.biz subdomain (line 48).
Flag: CDDC21{_10x_f0r_yOur_Serv!ce_}
Going Active (Reconnaissance)
4. VH2-1
I know you are getting tired, but don’t give up! This is your last task for now. Take a look at this web server, and let me know if you find anything.
hxxp://dev-01.globaldominationcorporation.xyz
The site given just displays a scary message saying we are not allowed to access it.

I first checked for subdomains using Sublist3r.
|
|
Output
|
|
Nice. But those internal subdomains all gave an unknown host error.
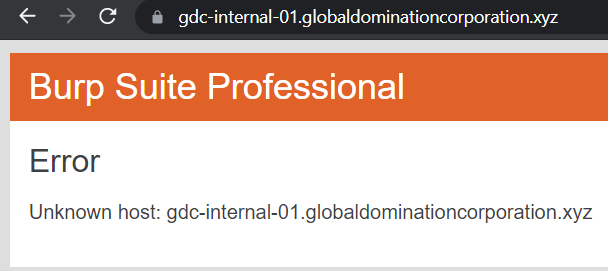
What’s going on here? I stared at the challenge title for long and then it clicked: VH stood for ‘Virtual Hosts’. Though all the subdomains discovered above (internal and public) are distinct websites, they are all probably hosted on a single server with just one IP address. One way the server can route our traffic to the correct website is by inspecting the
Host header in our HTTP request.Thus, we can perform a HTTP Host header attack where we send a HTTP request to the IP address of the public website dev-01.globaldominationcorporation.xyz but with the
Host header modified to the internal website gdc-internal-01.globaldominationcorporation.xyz .
Request to dev-01.globaldominationcorporation.xyz
|
|
Response
|
|
Flag: CDDC21{We1c0me_T0_VH2}
Linux Rules the World! (Linux)
1. Lock and Key
One of TheKeepers has successfully obtained what seems to be one of the GDC private servers. He has sent me the image and another file, but unfortunately, I’m not great with Linux. I think you’re the one for this mission.
Target: 13.213.91.240
Link: http://157.230.241.173/0x0301/iqWSmA/m1/file.zip
SHA256: a3fd0b01c5a12f830928cdd62bca7ab322610377c2b696f3313b734646bc2ae3
Inside the zip file is cybot01_bot1.key which contains an OpenSSH private key. I had no credentials to SSH with, so I googled and I came across this https://stackoverflow.com/questions/3818886/how-do-i-add-a-password-to-an-openssh-private-key-that-was-generated-without-a-p. Basically, ssh-keygen will show us the username to use as well as allow us to set a new password. After that, we can SSH in using the new private key file and retrieve the flag.
|
|
|
|
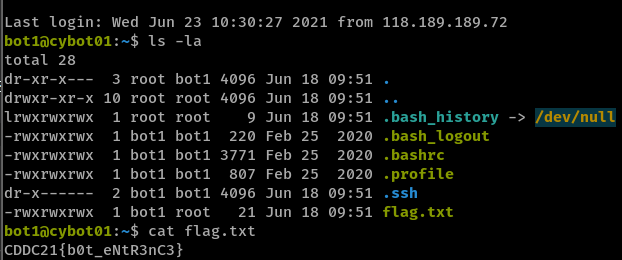
Flag:
CDDC21{b0t_eNtR3nC3}
Web Takedown Episode 1 (Web Vulnerabilities)
4. Traversal
I know that this server is vulnerable, but I can’t exploit it. Show your skills and find the right file.
Target URL: http://13.251.148.233/4HOF3DTV
The website contains navigation links which seem vulnerable to Local File Inclusion and Path Traversal attacks. The challenge title is also a big hint.
|
|
Interestingly, Burp Suite automatically solved this for me after I ran an “Active Scan” on the target website. It used the following payload to retrieve /etc/passwd:
|
|
|
|
Flag: CDDC21{!_like_the_PASSWD-F!le!}
5. Bypass
Finally, we have found an interesting web server used by the GDC, but I don’t have credentials so I can’t bypass the login page. I heard that you are the master of injections.
Target URL: http://13.251.148.233/D6IS1E8V
The website has a login form that gives a ‘No rows to show’ error message upon submission of invalid credentials.
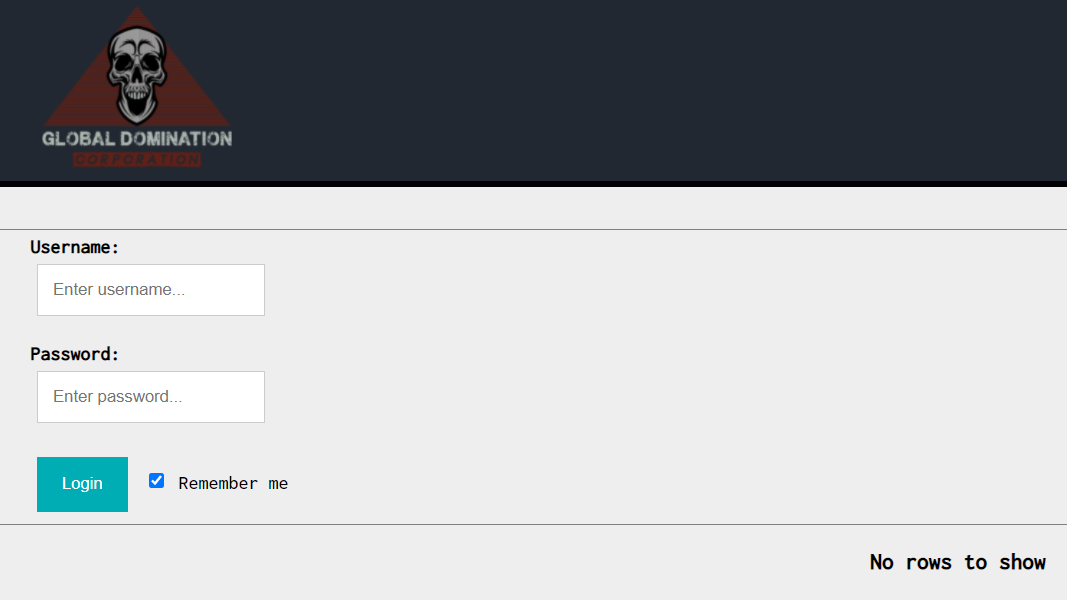
The concept of rows being selected suggests SQL is at play, and my teammate TheMythologist identified the SQL injection vulnerability to be present in the password parameter.
Request with single quote:
|
|
Response with 500 error:
|
|
Modifying our payload to username=test&password='+OR+'1'%3d'1&sub=&remember=on to match and return all rows gives us a new error message complaining of too many matches.
|
|
Limiting the number of returned rows to 1 by changing to password='+OR+'1'%3d'1'+limit+1--+ successfully returns credentials in the form of [[1,"john","cDR21afzss8"]] which unfortunately do not work.
Checking out the next row with password='+OR+'1'%3d'1'+limit+1,1--+, where the additional 1 parameter indicates offset, we get the flag: [[2,"flag","CDDC21{-Inject_Me-}"]].
Final payload:
|
|
Flag: CDDC21{-Inject_Me-}
Web Takedown Episode 2 (Web Vulnerabilities)
3. Restrictions
Strangely, the GDC allows this feature in their private web server. It looks pretty easy to exploit it. Let’s give it a try…
Target URL: http://18.139.27.125/H3YNQA42
The website has a file uploading feature. Uploads go under uploads/, and there is a file size check where Sorry, your file is too large or too small. is output if the check fails, but this shouldn’t hinder the rest of our solution. Attempting to upload a .php file returns an error message indicating that only JPG, JPEG, PNG and GIF files are allowed.
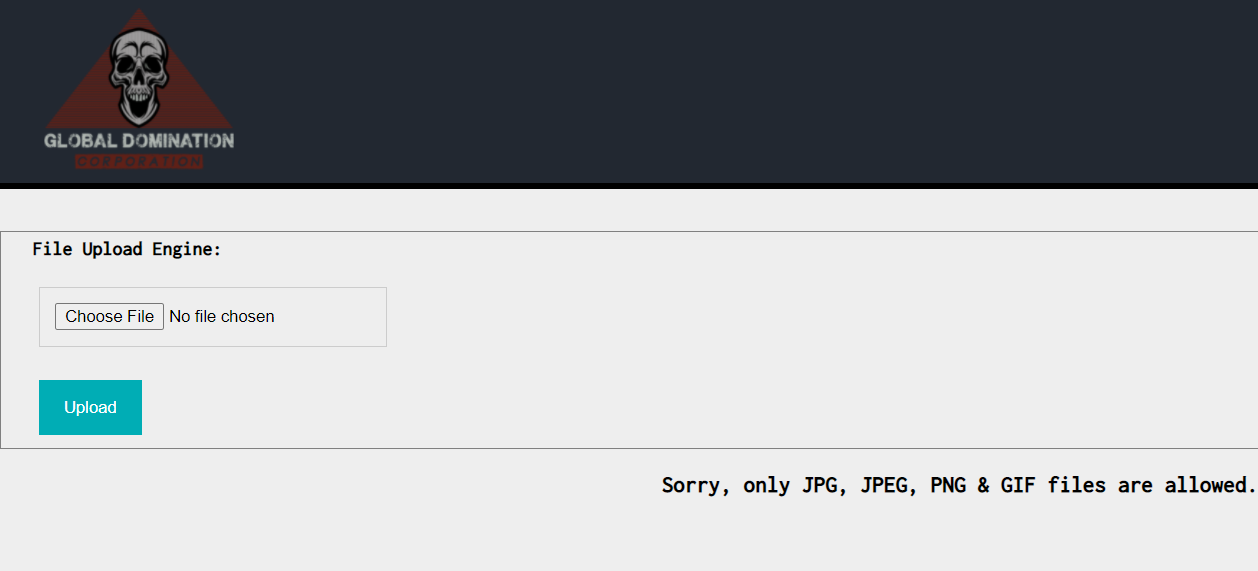
It is peculiar, then, that we can upload a
.txt file. This suggests that the file extension check is blacklist-based, rather than a whitelist of image extensions.
Request:
|
|
Response:
|
|
Since we just need to find an alternative to the blacklisted .php extension, we can try and use .phar as briefly pointed out here https://book.hacktricks.xyz/pentesting-web/file-upload#special-extension-tricks. Like .php, it is also a format for executing PHP code.
Using this neat PHP webshell from https://gist.github.com/joswr1ght/22f40787de19d80d110b37fb79ac3985, we upload our file and see that it has been accepted.
Request:
|
|
Response:
|
|
We can now access our webshell at http://18.139.27.125/H3YNQA42/uploads/1wpidnasd.phar.
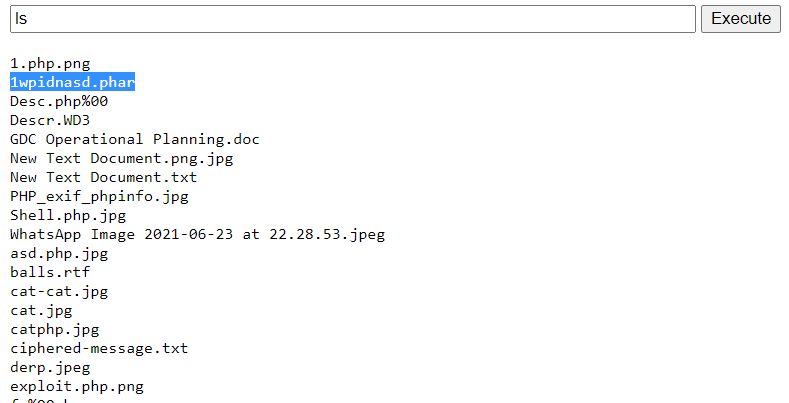
The flag is in the directory above.


Flag: CDDC21{s4F3_uPl04dZ}
File it Away (Pwn)
2. Smash It
One of the GDC servers was pawned by one of the resistance security teams years ago, and it seems their server is still up. We know it allows us to input messages, but we have never received any. We have given you the binary. Can you help us to understand what it expects to get?
Target: 13.213.195.207 port 60120
Link: http://157.230.241.173/0x0601/75k9tg/m2/file.zip
SHA256: bd5de768f001874a9dea5dbc8c19b1e1b51b684a812ec6bc304000f1de8f69bf
gdc_evidence_01 inside the ZIP file given is a x86 ELF binary. Below is the pseudocode generated by IDA:
|
|
User input is taken in and stored in a 64-byte stack-based buffer s by the gets function which does not have any bounds checking. The next stack-based variable v5 is then checked to be 'CDDC' for the flag to be printed.
Thus, this is a simple stack-based buffer overflow exploitation where our input in s can overflow into v5 and overwrite it with arbitrary data. We supply 64 characters to fully fill up the s buffer and then 4 more letters 'CDDC' to be written into v5.
|
|
Flag: CDDC21{st4ck_0v3wr1TiN8}
Post Mortem (Forensics)
2. Find The Code
Members of the Keepers group were able to capture some traffic. They believed it contained one of the secret codes. Help them find it.
Note: You need to insert the correct code to the flag structure. For example: CDDC21{code}
Link: http://157.230.241.173/0x0701/Eic0Sa/m2/file.zip
SHA256: 54c85637c324b5d297aa36196ff2102019baf74185ea505a90c9d435f1dcdfa3
I opened the given cap.pcap in Wireshark and took a look at the Protocol Hierarchy Statistics to get an overview of what kind of traffic the capture contained.
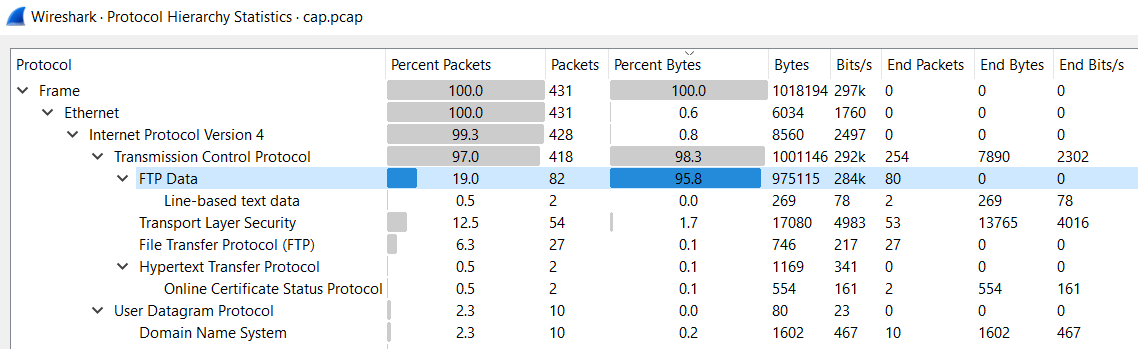
There is a good amount of FTP Data traffic so let’s first check that out with a
ftp display filter.
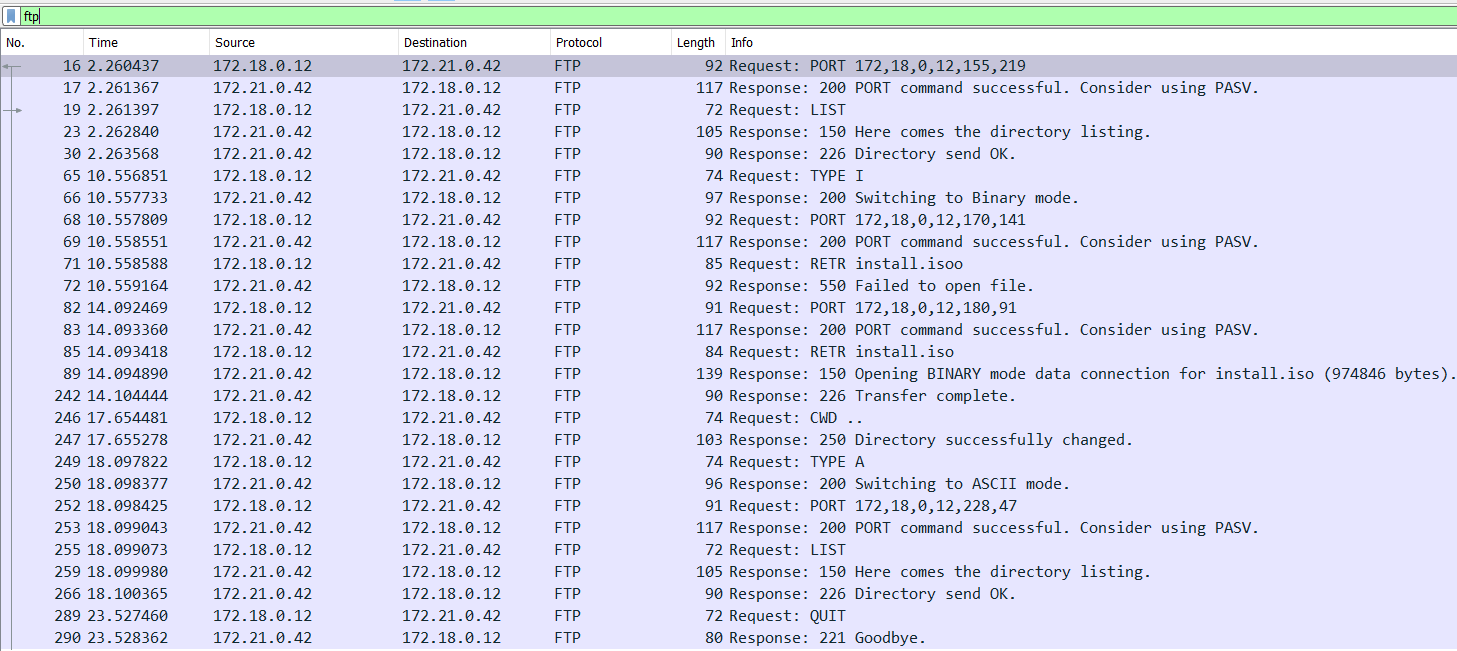
From the FTP command
RETR install.iso issued in packet 71 as well as the responses following it, we understand that the file install.iso is downloaded from the FTP server.Let’s follow the TCP stream of the FTP Data constituting
install.iso so that we can extract it out.
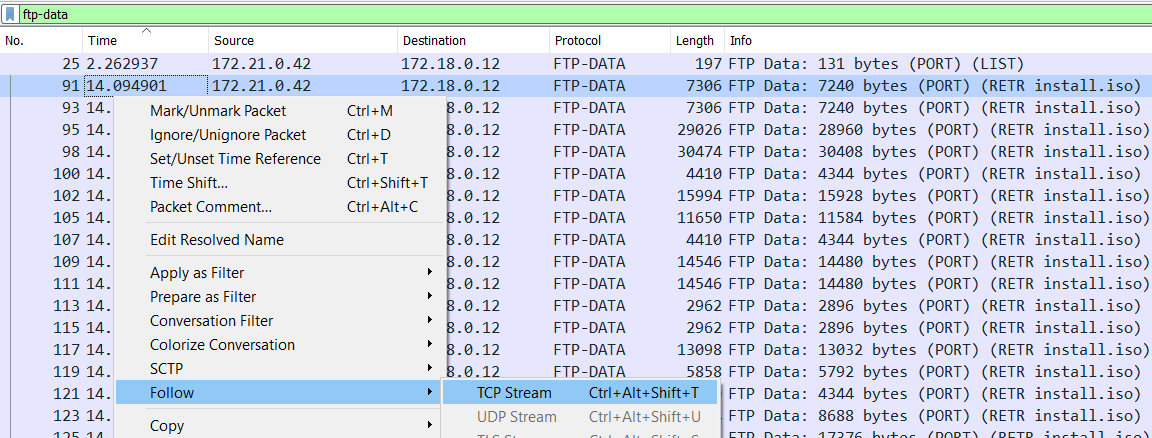
After extracting and saving
install.iso, I checked for its file format with Linux’s file command:
|
|
I googled for what to do with an EWF file and came across this https://www.andreafortuna.org/2018/04/11/how-to-mount-an-ewf-image-file-e01-on-linux/. So let’s get right into the commands needed to mount and view the image file.
Commands:
|
|
Image contents:
|
|
The code for the flag is then contained in Picture.png.
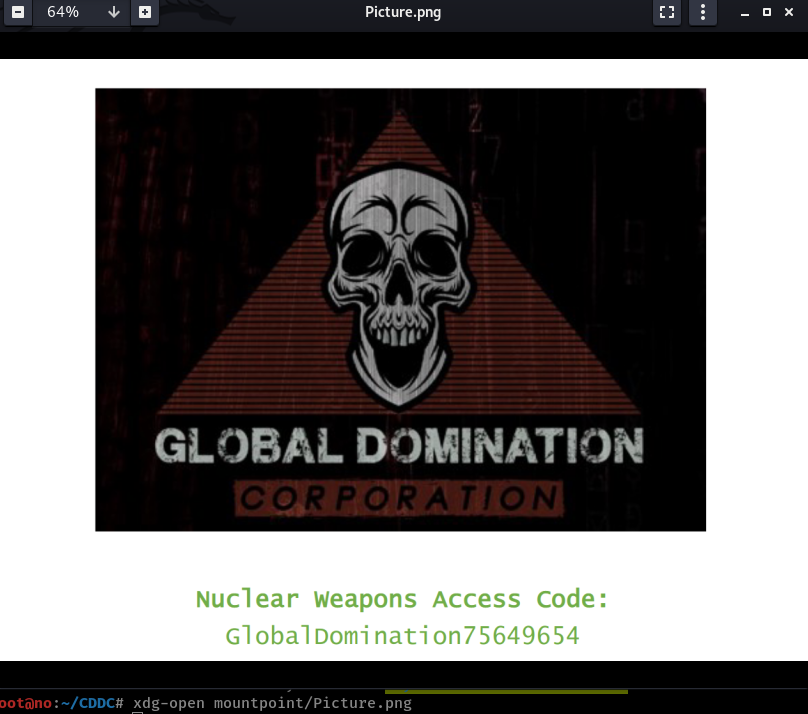
Flag:
CDDC21{GlobalDomination75649654}
3. WPA
The resistance has successfully intercepted encrypted WiFi traffic from a Cyber-BOT believed to communicate with the HQ. It is your task as a security analyst and cyber expert to decrypt the traffic and find out if there is any valuable information about the communication.
Link: hxxp://157.230.241.173/0x0701/fo5Nuj/m3/file.zip
SHA256: ab693cbac1da5489ff5b41e8672c8ed77015e11ca268dafc35e5310703359a6d
The given pcap.cap contains encrypted WPA IEEE 802.11 traffic. Since the capture contains the 802.11 authentication process with the EAPOL 4-way handshake in packets 340, 341, 343, and 345, and we know the SSID is CyBots as seen in packet 336, the steps to decrypt the traffic are almost the same as in this old challenge I did for UMDCTF 2021. The documentation referenced back then was this https://www.cisco.com/c/en/us/support/docs/wireless-mobility/80211/200527-Fundamentals-of-802-11-Wireless-Sniffing.html#anc63.
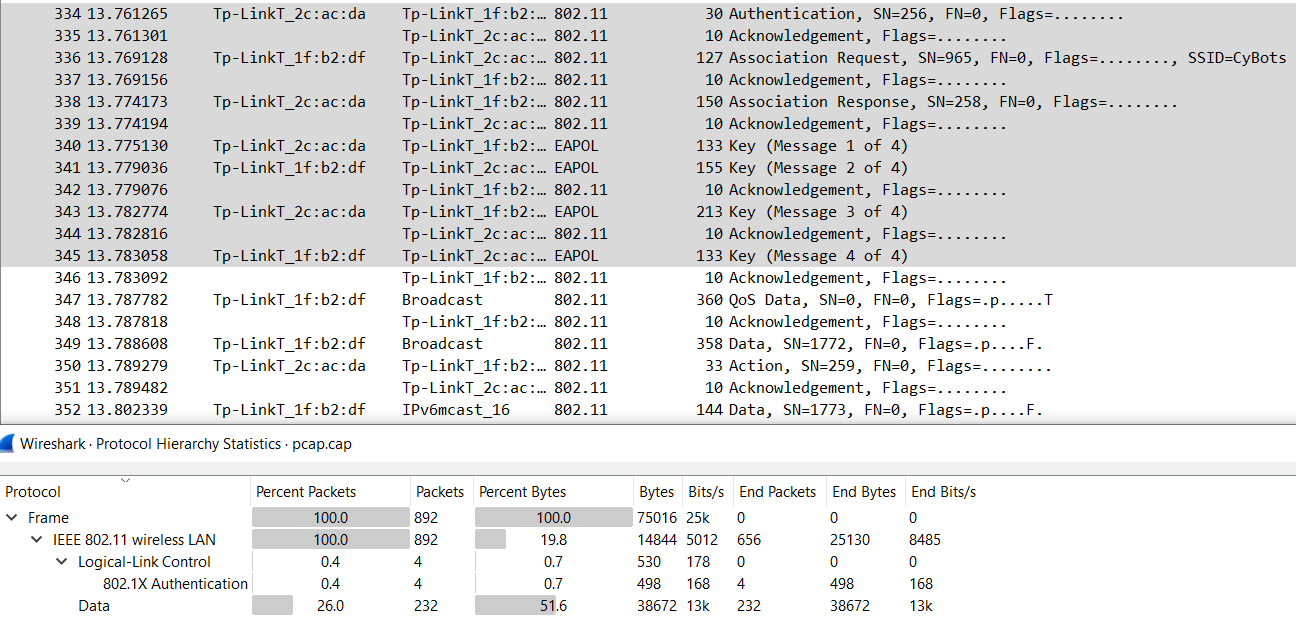
We first convert the network capture file to a format for cracking. In this case, the difference from the challenge in UMDCTF 2021 is that we use
-j to output to a format for John the Ripper instead of -z for a hashcat format.
|
|
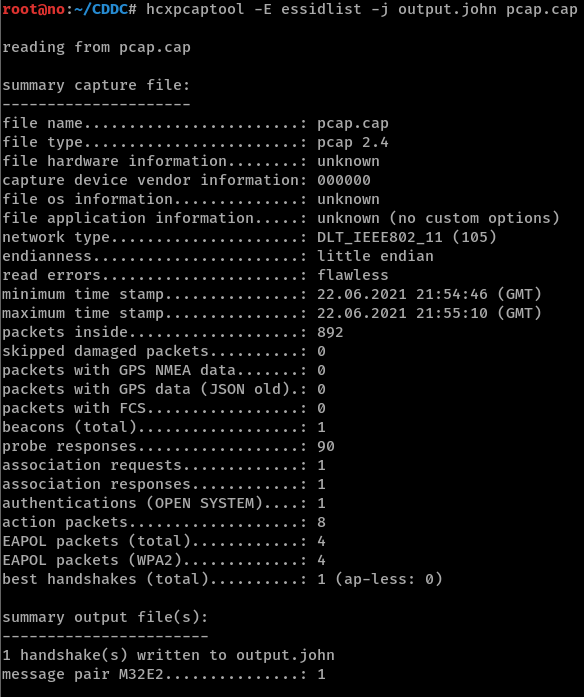
Then, we run
john on output.john and the WPA password is cracked to be 0123456789.
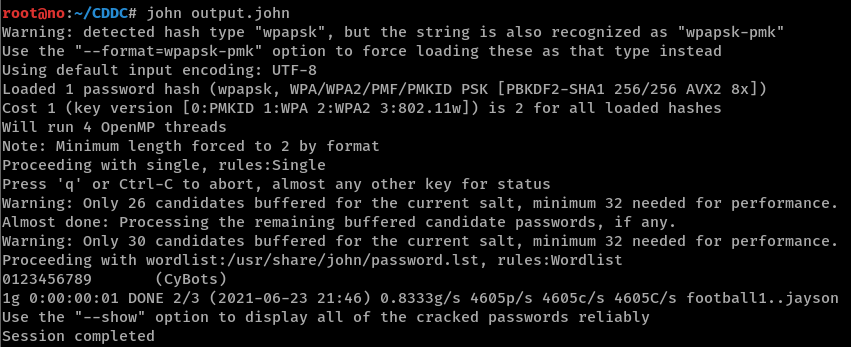
Now, we can enter the WPA password of
0123456789 as a decryption key for the IEEE 802.11 protocol in Wireshark’s preferences.
In the decrypted traffic, I looked at the HTTP object list and spotted an interesting HTML page with title ‘CDDC21’ and a flag emoji returned by 128.199.189.32 in packet 745.
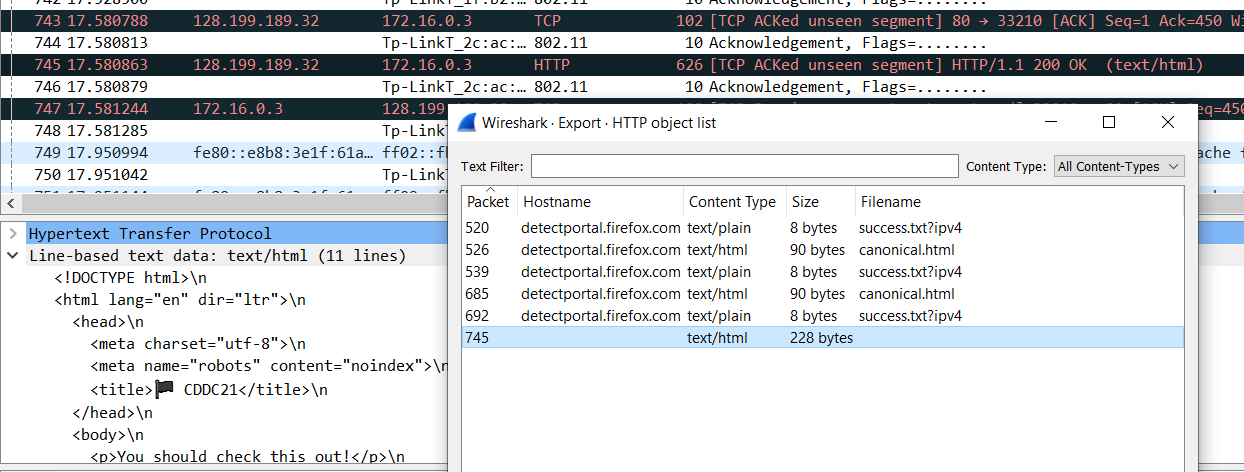
Visiting the site at http://128.199.189.32 gives us the flag.
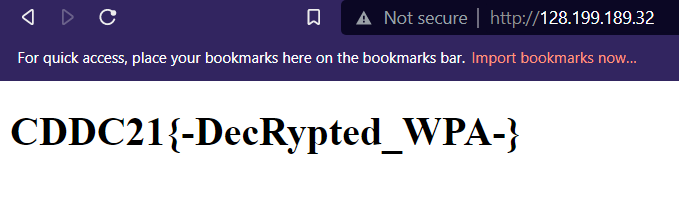
Flag:
CDDC21{-DecRypted_WPA-}
Behind the Mask (Windows)
1. Hello Guest
It’s time to expose the GDC! We have successfully obtained the IP address of their AD server. Enumerate the target machine and find the secret file.
Target IP Address: 54.255.213.169
Run nmap scan and see that SMB shares are available to explore via port 445.
|
|
Output:
|
|
Since the challenge title says ‘Guest’, I assumed we were expected to authenticate to the SMB shares with the guest account (which by default has no password).
While we could connect using smbclient -U guest -L //54.255.213.169, I found crackmapexec and smbmap to be better tools.
crackmapexec tells us what shares there are and what permissions we have for them.
|
|
Output:
|
|
We have read permissions to a Backup share, so let’s recursively list the contents of this share with smbmap.
|
|
Output:
|
|
Both .txt files seem interesting so let’s download them.
|
|
flag.txt contains the flag while Alex.txt contains what appears to be credentials:
|
|
Flag: CDDC21{0LLHE_Gue$T}
2. Old Memories
The file you have found in the shared folder looks like a memory dump that may contain user passwords. You need these passwords for your next mission.
With the new alexander.p credentials obtained from stage 1. Hello Guest, we recheck our permissions for the shares and find that we have read permissions for the interestingly-named Forensics1 share now.
|
|
Output:
|
|
Listing the contents of the share:
|
|
Output:
|
|
lsass.zip is interesting and contains lsass.DMP. This is the memory dump mentioned in the challenge description and it is of the lsass.exe process which we can extract credentials from using tools like mimikatz for Windows or pypykatz for Linux.
|
|
and we basically get two credentials in the output – one of which contains the flag:
|
|
Flag: CDDC21{lsa$$_DUMP_password}
4. Last Note
We just need to find the final piece of information. Use the credentials you have found so far and list all the GDC users configured on the server.
My teammate TheMythologist solved this one. The solution uses John’s credentials obtained from stage 2. Old Memories. Using enum4linux to enumerate and list all users’ information, we find the flag in the description of henry.s’s account on line 12.
|
|
|
|
Flag: CDDC21{We!!_D0NE}
Thanks for reading as always :)