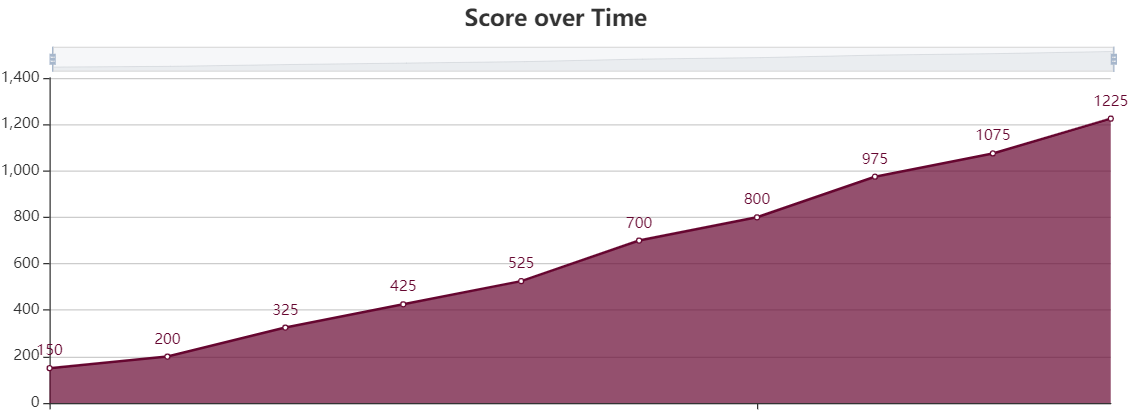
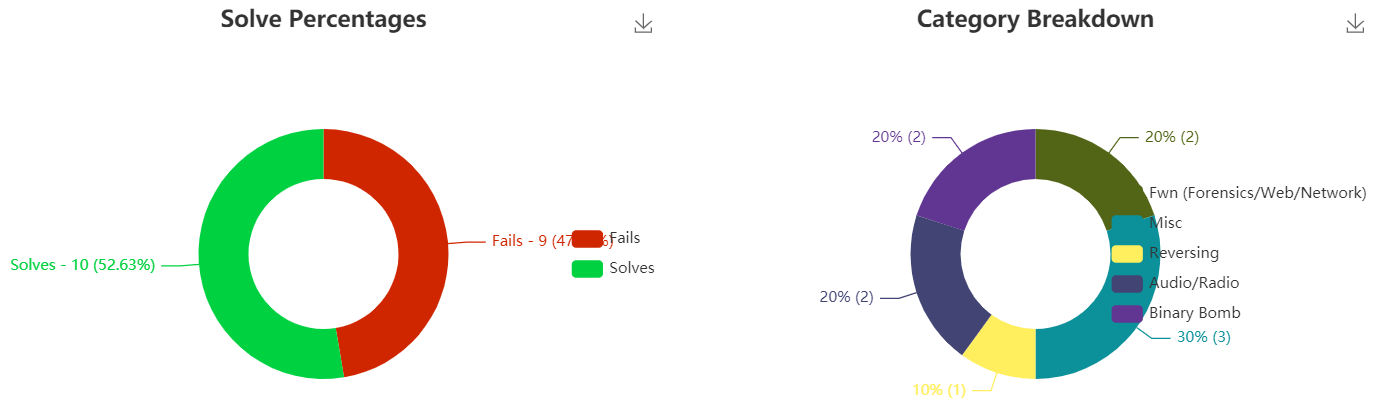
Thanks organizers! I enjoyed the Binary Bomb reversing challenges. We got 13th place. Sadly solved less for this one but it was fun trying some RE which I usually avoid. My 9 failed solves were because of Toilet Humor 5.
🎵 Armin van Buuren feat. RBVLN - Weight Of The World (Club Mix) powered me during this CTF :)
| Details | Links |
|---|---|
| CTFtime.org Event Page | https://ctftime.org/event/1319/ |
Reversing
Who am I?
I hid my flag in this program but it seems to have forgot who it is?
Author: Percival
Attached: who_am_i.exe
Rough pseudocode generated by IDA with some variables renamed by me:
|
|
The flag is stored in flag_buf as shown in line 15, and is written to by the xor_flag_1 and xor_flag_2 functions in line 41 and 47 respectively. .
xor_flag_2 retrieves bytes from byte_4F7B40:
|
|
which shows up as byte_4F7B40 db 27h, 4Ch, 35h, 55h, 4Bh, 1, 4Bh, 47h, 5, 7 dup(0). xor_flag_1 also retrieves bytes from another location. While we could figure out what kind of inputs to give to manoeuvre through the switch cases, we can just assemble the bytes from both locations and xor them again with 0x78 to get the flag:
|
|
Flag: DawgCTF{hU_4M-3y3?}
Binary Bomb
BBomb - Phase 6
Oh no… I lost the key to my string again :(
Author: treap_treap
Generated pseudocode with IDA and variables renamed by me. I also redefined the 24 variables at the beginning to be part of a single string structure:
|
|
It’s just mainly some simple bitwise operations in lines 31-32, so we can replicate the decoding routine in Python except that we will additionally bruteforce for each char to match each byte in string. This is basically finding out what input given to calloc_buf gives back the bytes stored in the str structure in the C code.
|
|
Flag: DawgCTF{B1t_Man1pUlaTi0n_1$_Fun}
Binary Bomb - Bonus Phase!
But wait… there’s more!
Author: treap_treap
strings the binary with any tool of your preference (I used IDA) and you could probably find the flag somehow.
Flag: Pr3e7Y_57E4ltHy_Fl4g
Fwn (Forensics/Web/Network)
These Ladies Paved Your Way
Per womenintech.co.uk, these 10 women paved your way as technologists. One of them holds more than 100 issued patents and is known for writing understandable textbooks about network security protocols. What other secrets does she hold?
Author: Clearedge
Attached: WomenInTech.zip
Zip file contains various images of prominent women in fields of technology:
|
|
Google searching for the woman who holds more than 100 issued patents and knows much about network security protocols leads us to Radia Perlman.
Viewing the Exif metadata with http://exif.regex.info/exif.cgi, we get a Base64-encoded string under Credit and what seems to be the enciphered flag under Keywords:
| IPTC | |
|---|---|
| Credit | U3Bhbm5pbmdUcmVlVmlnCg== |
| Application | Record Version 4 |
| Keywords | VpwtPBS{r0m5 0W t4x3IB5} |
The Base64-decoded string is SpanningTreeVig, which hints us to Vigenère-decode the flag with a key of SpanningTreeVig.
Flag:DawgCTF{l0t5 0F p4t3NT5}
Crack IFS
The accounts in this QNX IFS have insecure passwords. Crack them to assemble the flag.
https://www.qnx.com/developers/docs/7.0.0/#com.qnx.doc.neutrino.building/topic/intro/intro_ifs.html
DawgCTF.ifs: hxxps://drive.google.com/file/d/1imS0_LQTWg67bwZucoSSa9US28C1uAI2/view?usp=sharing
Author: Percival
We can use this dumpifs tool https://github.com/askac/dumpifs to dump files. Command line switches are detailed here: http://www.qnx.com/developers/docs/7.0.0/index.html#com.qnx.doc.neutrino.utilities/topic/d/dumpifs.html . -x and -b extracts the files while -d specifies the output directory.
|
|
We now have the /etc/shadow file dumped which contains the password hashes:
|
|
Looking at the various hash formats listed on https://hashcat.net/wiki/doku.php?id=example_hashes , I guessed the format to be 1500 descrypt, DES (Unix), Traditional DES 48c/R8JAv757A. Through my initial dictionary attack attempts using rockyou.txt which failed to recover all the passwords, I found out that the passwords were just 4-letter segments so I switched to a hashcat bruteforce mask attack with the charset of printable characters and a length of 4.
|
|
Flag: DawgCTF{un_scramble}
Misc
Identifications
Hey man. I’m standing in front of this Verizon central office building. What’s its CLLI code?
What? No, I don’t know where I am, my GPS is broken. I tried to connect to some Wi-Fi so I could download a map or something, but I don’t know the password to any of these networks.
identifications.7z: hxxps://drive.google.com/file/d/1YkzVIwbNKWKG4I0K8F_J8DCC9mqBn2ET/view?usp=sharing
Once you figure out the CLLI code, make sure to wrap it in DawgCTF{}.
Author: nb
The .7z contains two images: 1 of the supposed Verizon central office building and 1 of a screen listing details of various Wi-Fi access points nearby.

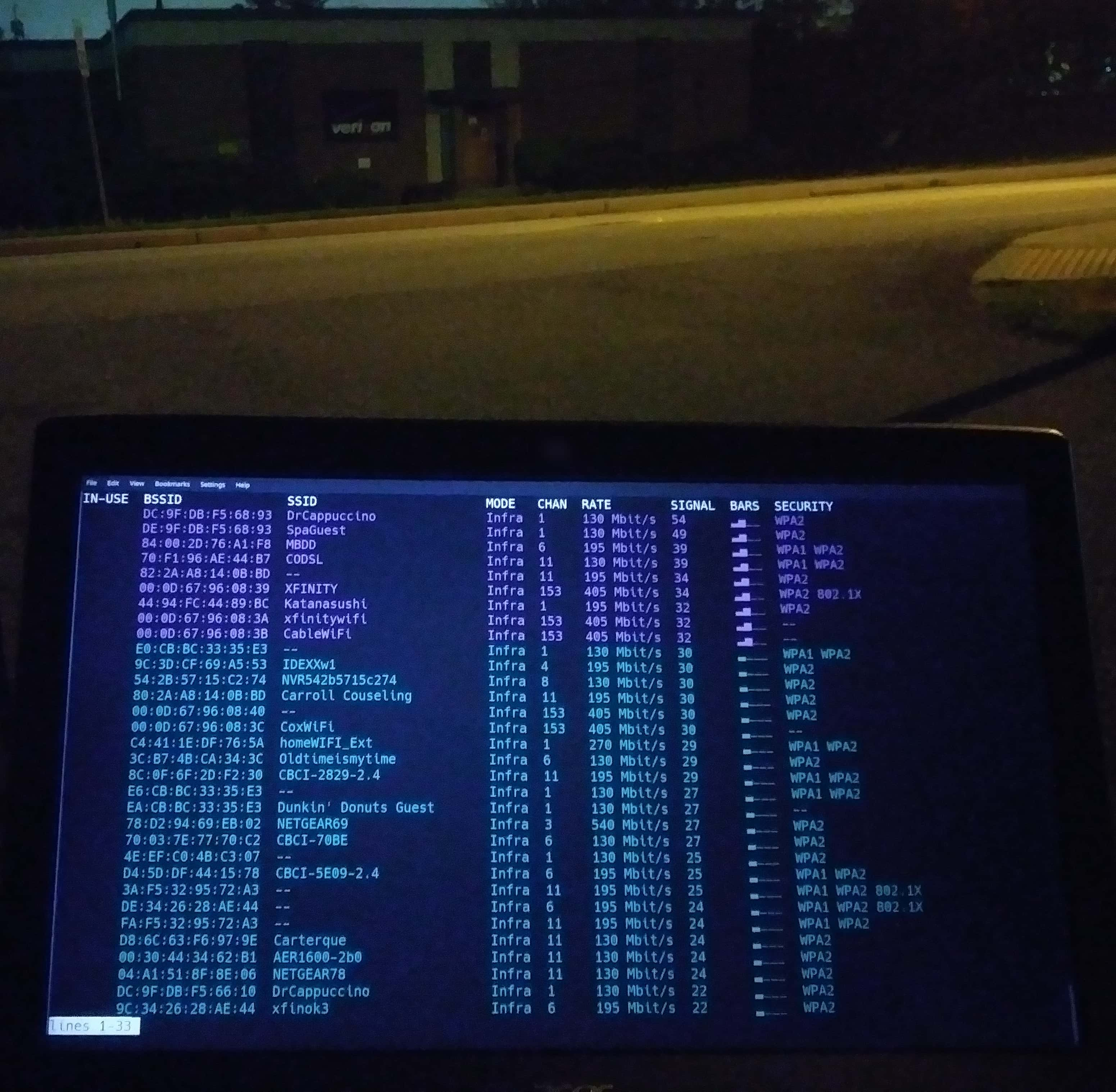
Google searching the Dr Cappuccino SSID sends us to https://www.drcappuccino.com/ which is located at 1304 South Main St. | Mount Airy, MD 21771 as listed under their contact page.
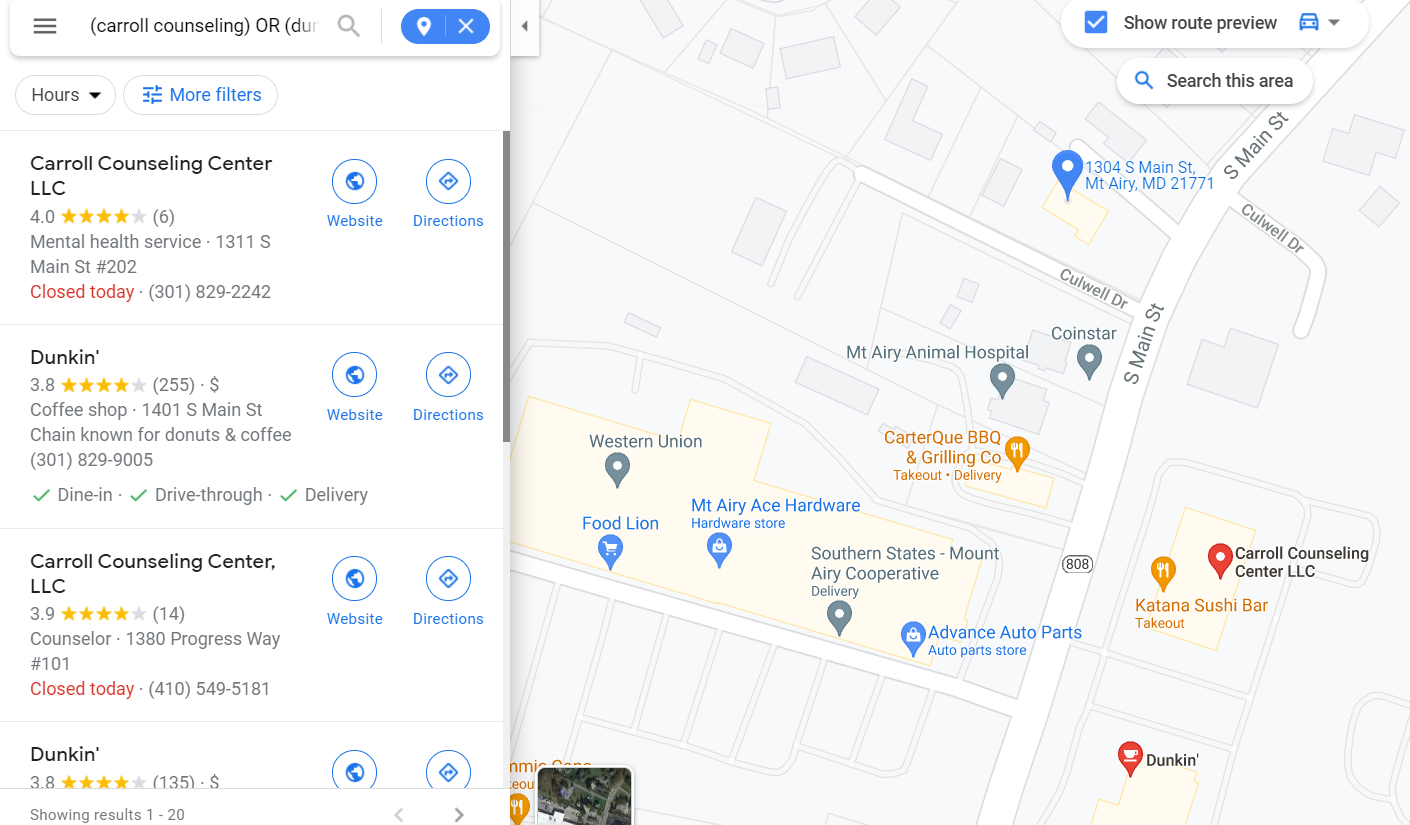
Plugging that address into Google Maps, we can confirm that other stores like Katana Sushi Bar, Carroll Counseling Center LLC and Dunkin' Donuts displayed in the image of Wi-Fi details are located here too.
Looking up for Verizon Central Offices in the city of Mount Airy gives us this nice table https://www22.verizon.com/wholesale/attachments/space-exhaust/WebUpdateSouth.pdf where we can search for Mount Airy and get the corresponding CLLI code in the 3rd column.
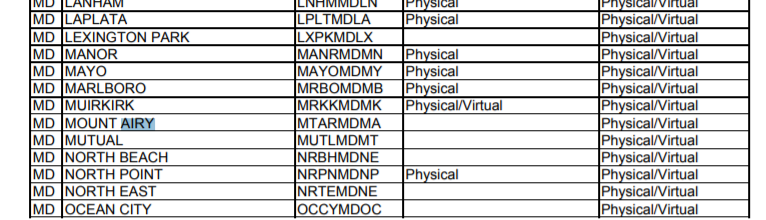
Flag: DawgCTF{MTARMDMA}
Toilet Humor 5
The flag is five poops
Author: toomanybananas
Self-explanatory and pretty dumb.
Flag: DawgCTF{5️⃣💩}
The Rain in Spain
I installed this cool IoT-enabled weathervane on my boat for sailing around Málaga, but the sensors seem to be giving erratic readings…
Author: Noodle
Attached: spain.csv
Plot a graph with the given .csv file using https://www.csvplot.com/ and play around with the axes to display the flag nicely.
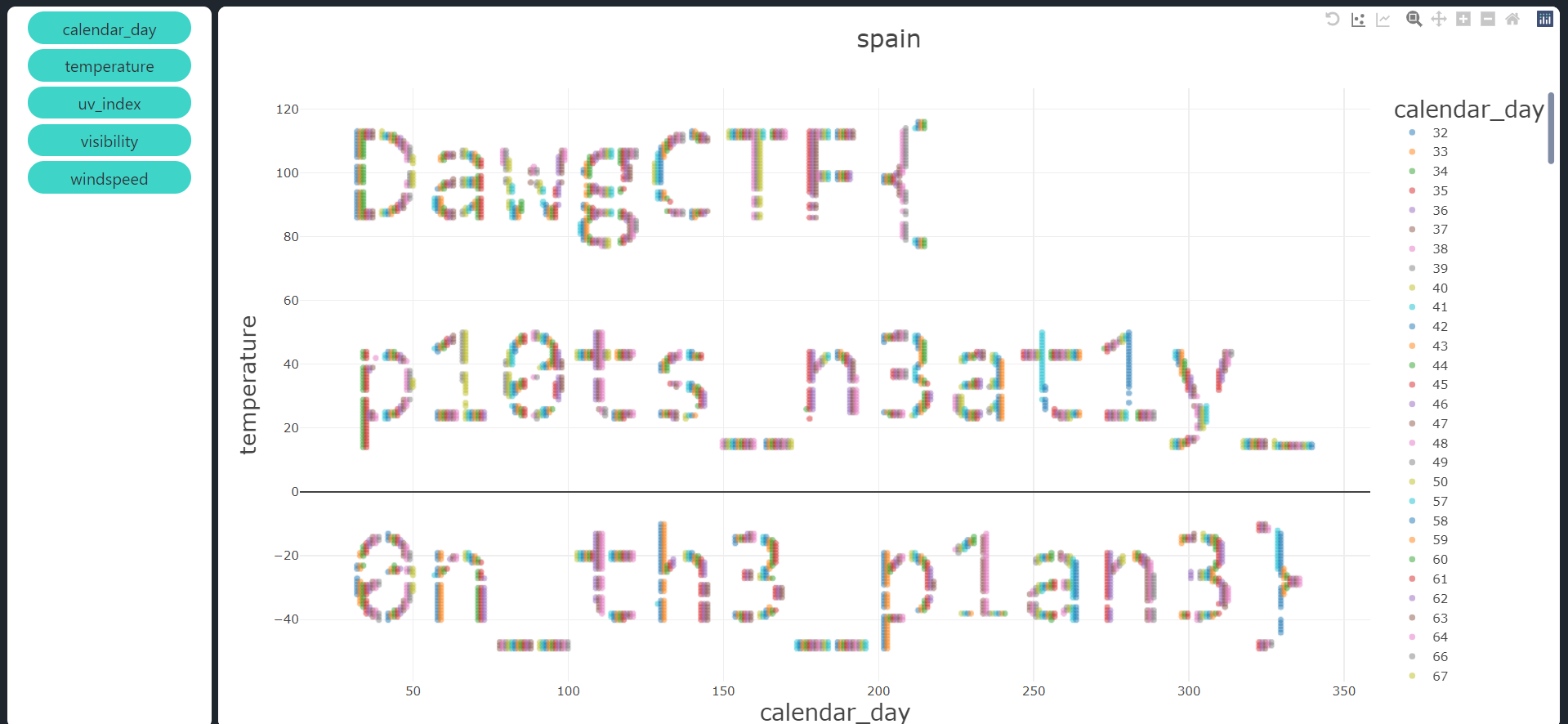
Flag: DawgCTF{p10ts_n3at1y_0n_th3_p1an3}
Audio/Radio
Moses
If you can find a way to part the waves, you might find something on the seafloor.
moses.zip: hxxps://drive.google.com/file/d/1c6uEmcRssq2FKmQqNYNJ3NRvK6t_KVAd/view?usp=sharing
Author: Noodle
The .zip file contains moses1.flac and moses2.flac with almost identical spectrograms. This is viewed using Spek.
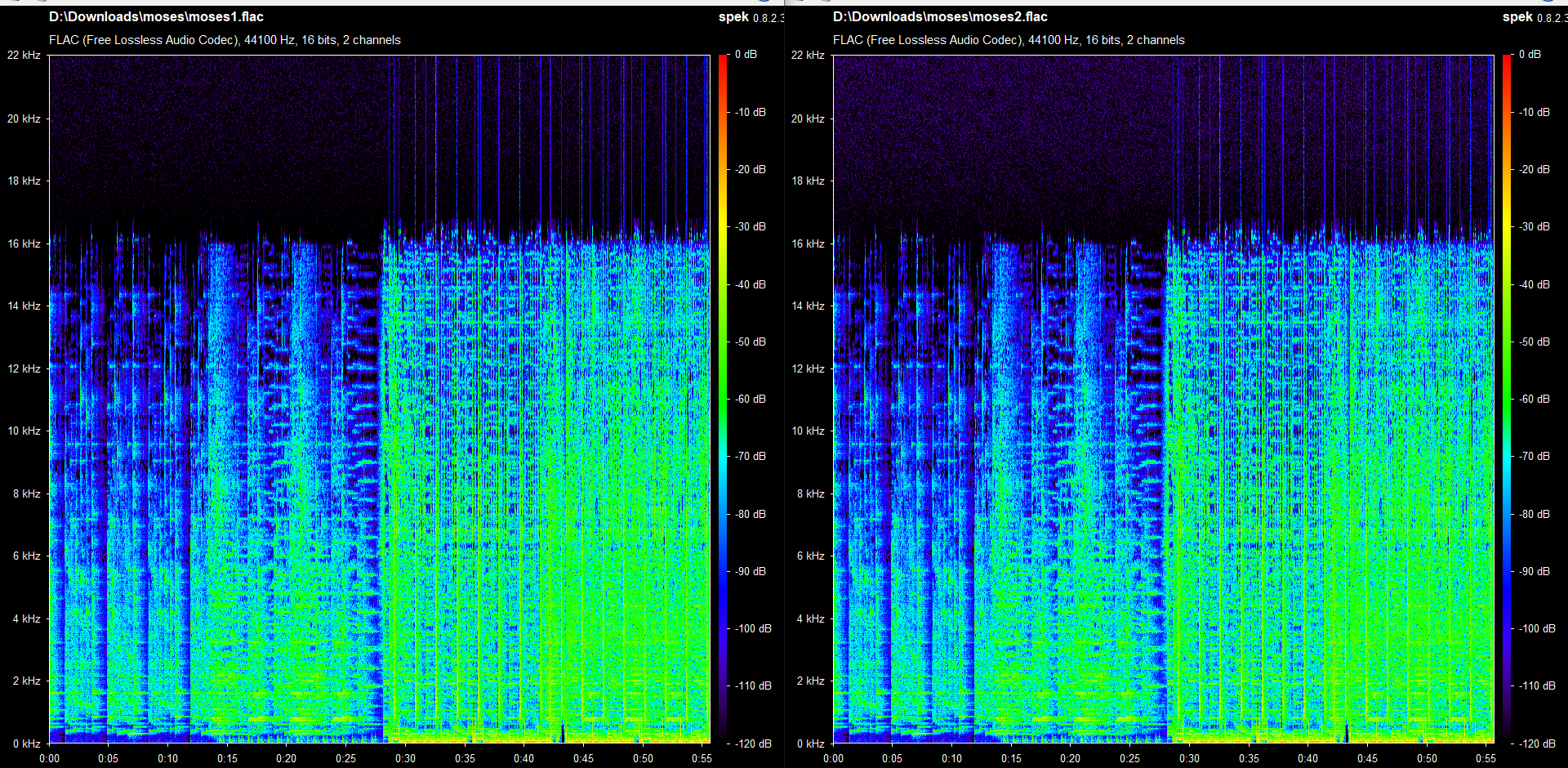
To find out the difference between these 2 audios, we can do a phase inversion in Audacity.
- Import both tracks into Audaciity
- Select one track and apply the Invert Effect on it.
- Select both tracks and Mix and Render
- Export the new track
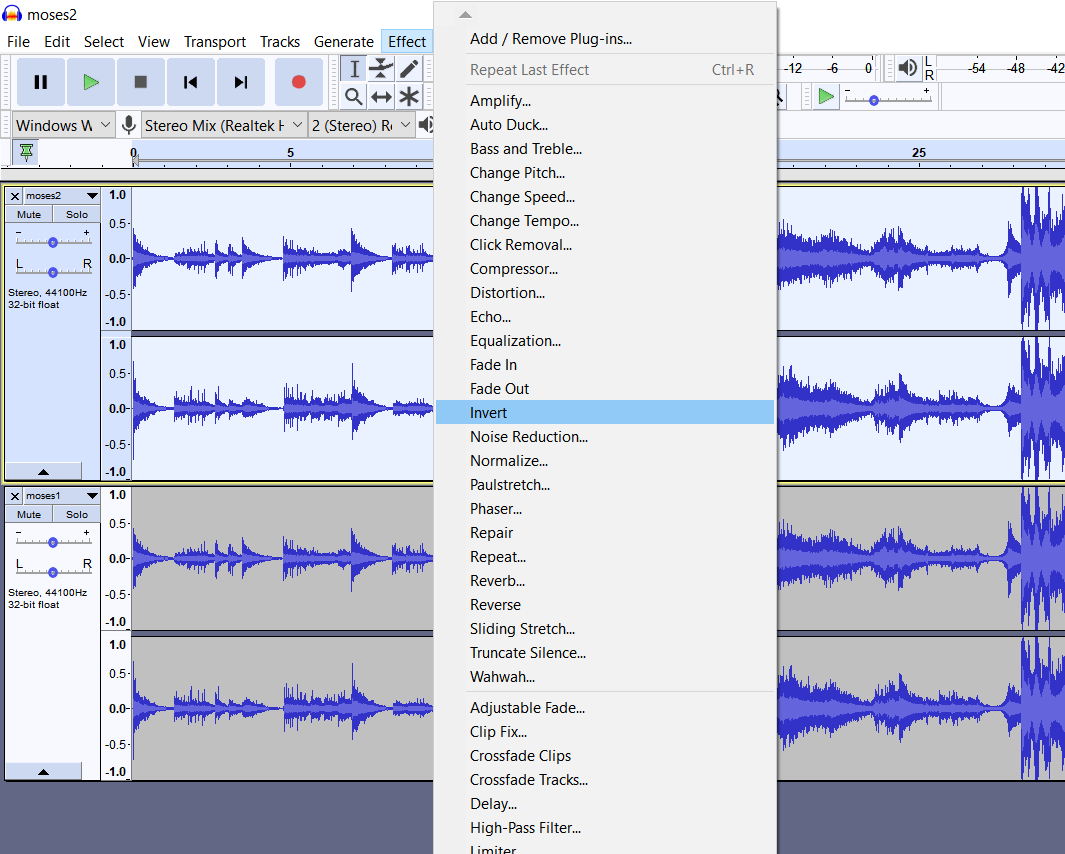
The flag is now at the bottom of the spectrogram of the new track.
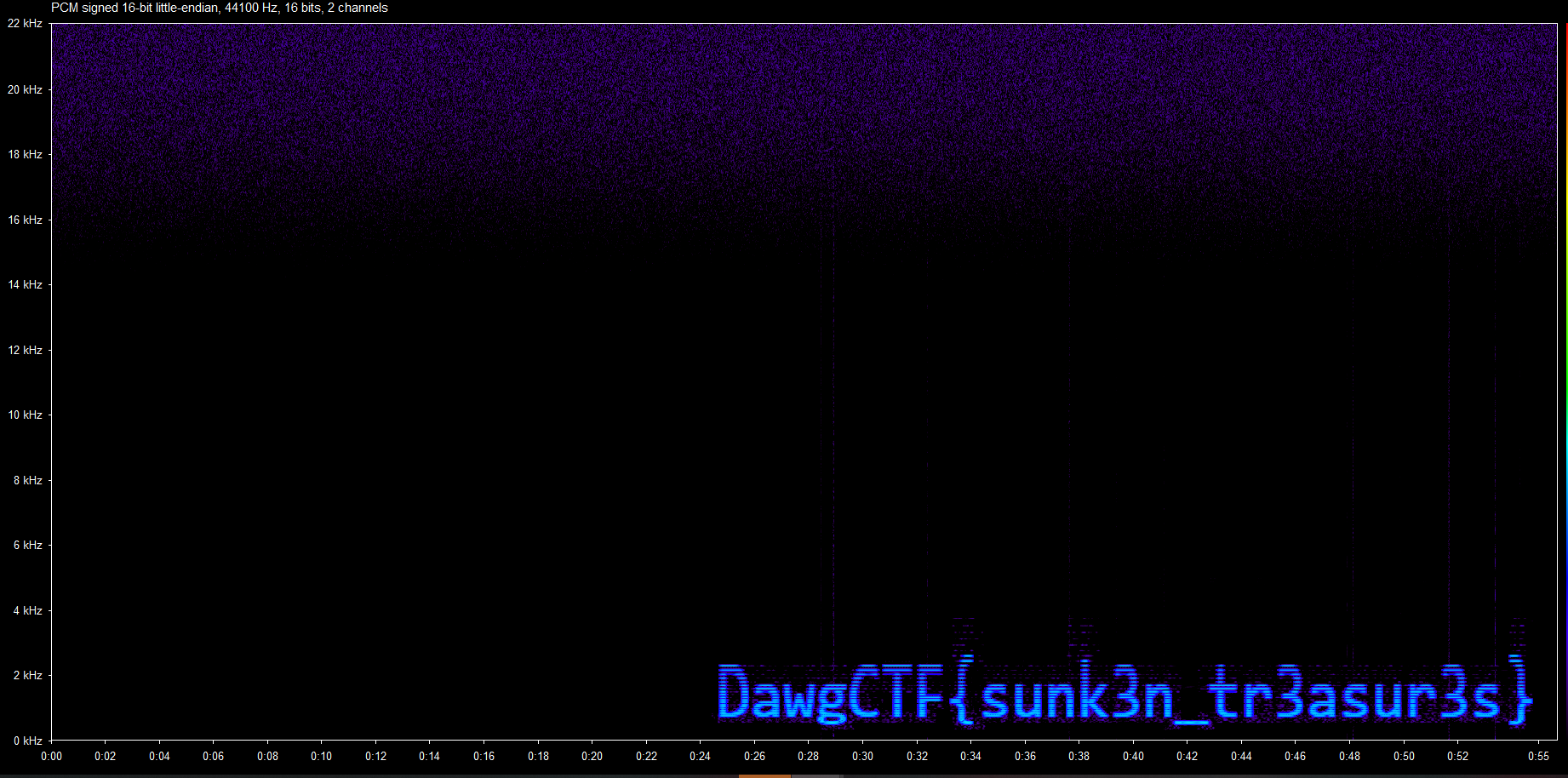
Flag: DawgCTF{sunk3n_tr3asur3s}
Deserted Island Toolkit
What would a drunken sailor do? (Wrap the output in DawgCTF{ })
DesertedIslandToolkit.zip: hxxps://drive.google.com/file/d/1vYUIAPIeQgE6x781tH6SU3uU0YSx5Yxv/view?usp=sharing
Author: Eyeclept
The .zip contains these standard CD files:
|
|
The .cdda file contains audio data so let’s convert it to a listenable format with https://convertio.co/cdda-wav/
The audio is then a series of short and long tones which we can immediately suspect to be Morse Code:
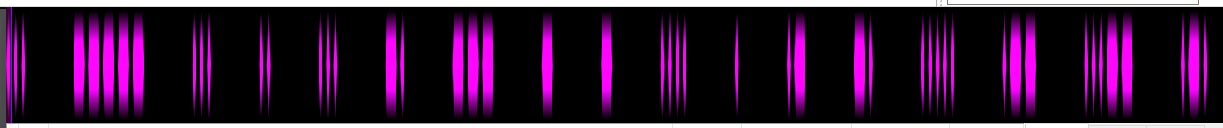
which was transcribed as... ----- ... .. ... -. --- - - .... . .- -. ..... .-- ...-- .-. and decoded to be S0SISNOTTHEAN5W3R
Flag: DawgCTF{S0SISNOTTHEAN5W3R}
That’s all! Hope you enjoyed :)