Thanks drome for sharing his knowledge and skills! He completed all 10 challenges and this series of writeups is done by him :)
| Details | Links |
|---|---|
| Official Challenge Site | https://flare-on.com/ |
| Official Challenge Announcement | https://www.fireeye.com/blog/threat-research/2021/08/announcing-the-eighth-annual-flare-on-challenge.html |
| Official Solutions | https://www.mandiant.com/resources/flare-on-8-challenge-solutions |
| Official Challenge Binaries | http://flare-on.com/files/Flare-On8_Challenges.zip |
05_FLARE_Linux_VM
Because of your superior performance throughout the FLARE-ON 8 Challenge, the FLARE team has invited you to their office to hand you a special prize! Ooh – a special prize from FLARE ? What could it be? You are led by a strong bald man with a strange sense of humor into a very nice conference room with very thick LED dimming glass. As you overhear him mumbling about a party and its shopping list you notice a sleek surveillance camera. The door locks shut!
Excited, you are now waiting in a conference room with an old and odd looking computer on the table. The door is closed with a digital lock with a full keyboard on it.
Now you realise… The prize was a trap! They love escape rooms and have locked you up in the office to make you test out their latest and greatest escape room technology. The only way out is the door – but it locked and it appears you have to enter a special code to get out. You notice the glyph for U+2691 on it. You turn you attention to the Linux computer - it seems to have been infected by some sort of malware that has encrypted everything in the documents directory, including any potential clues.
Escape the FLARE Linux VM to get the flag - hopefully it will be enough to find your way out.
Hints:
- You can import “FLARE Linux VM.ovf” with both VMWare and VirtualBox.
- Log in as ‘root’ using the password ‘flare’
- If you use VirtualBox and want to use ssh, you may need to enable port forwarding. The following link explains how to do it: https://nsrc.org/workshops/2014/btnog/raw-attachment/wiki/Track2Agenda/ex-virtualbox-portforward-ssh.htm7zip password:
flare
The VM is running OpenSUSE. When we run and log in to the VM, we get a very restrictive CLI interface that doesn’t allow us to scroll or copy text, so we want to be able to access the file system directly.
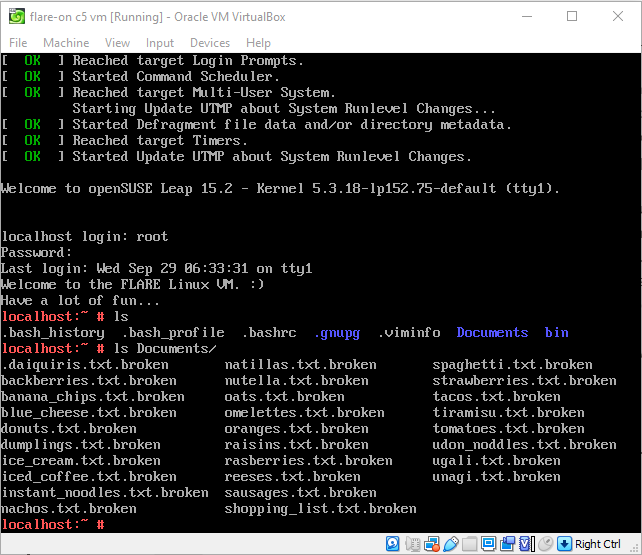
We configure the port forwarding settings on the VM according to the instructions, then log in using WinSCP, then browse through the files, and copy any interesting files to host for deeper analysis if needed.
Interesting files
/root/.bash_history
|
|
zypper is the command line package manager for OpenSUSE.
/root/.bash_profile
|
|
/root/.bashrc
|
|
/root/.viminfo
# This viminfo file was generated by Vim 8.0.
# You may edit it if you're careful!
# Viminfo version
|1,4
# Value of 'encoding' when this file was written
*encoding=latin1
# hlsearch on (H) or off (h):
~h
# Command Line History (newest to oldest):
:q
|2,0,1629990288,,"q"
:wq
|2,0,1629990117,,"wq"
# Search String History (newest to oldest):
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Debug Line History (newest to oldest):
# Registers:
# File marks:
'0 1 0 /tmp/crontab.S2jaym
|4,48,1,0,1629990288,"/tmp/crontab.S2jaym"
'1 1 0 ~/.bash_history
|4,49,1,0,1629990187,"~/.bash_history"
'2 1 23 /tmp/crontab.uM22lg
|4,50,1,23,1629990117,"/tmp/crontab.uM22lg"
'3 3 16 ~/.bash_profile
|4,51,3,16,1629989986,"~/.bash_profile"
# Jumplist (newest first):
-' 1 0 /tmp/crontab.S2jaym
|4,39,1,0,1629990288,"/tmp/crontab.S2jaym"
-' 1 0 ~/.bash_history
|4,39,1,0,1629990187,"~/.bash_history"
-' 1 0 ~/.bash_history
|4,39,1,0,1629990187,"~/.bash_history"
-' 1 23 /tmp/crontab.uM22lg
|4,39,1,23,1629990117,"/tmp/crontab.uM22lg"
-' 1 23 /tmp/crontab.uM22lg
|4,39,1,23,1629990117,"/tmp/crontab.uM22lg"
-' 1 23 /tmp/crontab.uM22lg
|4,39,1,23,1629990117,"/tmp/crontab.uM22lg"
-' 1 23 /tmp/crontab.uM22lg
|4,39,1,23,1629990117,"/tmp/crontab.uM22lg"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 3 16 ~/.bash_profile
|4,39,3,16,1629989986,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
-' 1 0 ~/.bash_profile
|4,39,1,0,1629989976,"~/.bash_profile"
# History of marks within files (newest to oldest):
> /tmp/crontab.S2jaym
* 1629990286 0
" 1 0
> ~/.bash_history
* 1629990186 0
" 1 0
> /tmp/crontab.uM22lg
* 1629990116 0
" 1 23
^ 1 24
. 1 23
+ 1 23
> ~/.bash_profile
* 1629989986 0
" 3 16
^ 3 17
. 3 16
+ 3 16
Cron is the Linux command line
|
|
/var/spool/cron/tabs/root
# DO NOT EDIT THIS FILE - edit the master and reinstall.
# (/tmp/crontab.uM22lg installed on Thu Aug 26 15:01:57 2021)
# (Cronie version 4.2)
* * * * * /usr/lib/zyppe
Crontab
The crontab command opens the cron table, table is the list of tasks scheduled to run at regular time intervals on the system, for editing.
localhost:~ # crontab -l
* * * * * /usr/lib/zyppe
Searching by datetime range
Since we know the date the files were encrypted, we can also search the file system for files modified on that date using find.
localhost:~ # find / -type f -newermt '2021-08-26' ! -newermt '2021-08-27' 2>/dev/null
/.snapshots/2/grub-snapshot.cfg
/.snapshots/3/grub-snapshot.cfg
/.snapshots/4/grub-snapshot.cfg
/.snapshots/5/grub-snapshot.cfg
/.snapshots/5/info.xml
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Basenames
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Conflictname
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Dirnames
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Group
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Installtid
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Name
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Packages
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Providename
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Recommendname
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Requirename
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Sha1header
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Sigmd5
/.snapshots/6/snapshot/usr/lib/sysimage/rpm/Suggestname
/.snapshots/6/snapshot/etc/sysconfig/cron
/.snapshots/6/info.xml
/.snapshots/6/grub-snapshot.cfg
/.snapshots/6/filelist-5.txt
/.snapshots/grub-snapshot.cfg
/root/Documents/backberries.txt.broken
/root/Documents/banana_chips.txt.broken
/root/Documents/blue_cheese.txt.broken
/root/Documents/donuts.txt.broken
/root/Documents/dumplings.txt.broken
/root/Documents/ice_cream.txt.broken
/root/Documents/iced_coffee.txt.broken
/root/Documents/instant_noodles.txt.broken
/root/Documents/nachos.txt.broken
/root/Documents/natillas.txt.broken
/root/Documents/nutella.txt.broken
/root/Documents/oats.txt.broken
/root/Documents/omelettes.txt.broken
/root/Documents/oranges.txt.broken
/root/Documents/raisins.txt.broken
/root/Documents/rasberries.txt.broken
/root/Documents/reeses.txt.broken
/root/Documents/sausages.txt.broken
/root/Documents/shopping_list.txt.broken
/root/Documents/spaghetti.txt.broken
/root/Documents/strawberries.txt.broken
/root/Documents/udon_noddles.txt.broken
/root/Documents/ugali.txt.broken
/root/Documents/unagi.txt.broken
/root/Documents/.daiquiris.txt.broken
/root/Documents/tacos.txt.broken
/root/Documents/tiramisu.txt.broken
/root/Documents/tomatoes.txt.broken
/root/.bashrc
/root/.bash_profile
/var/cache/salt/minion/rpmdb.cookie
/var/cache/zypp/solv/@System/cookie
/var/cache/zypp/solv/@System/solv
/var/cache/zypp/solv/@System/solv.idx
/var/cache/zypp/solv/repo-update/solv
/var/cache/zypp/solv/repo-update/solv.idx
/var/cache/zypp/solv/repo-update/cookie
/var/cache/zypp/solv/repo-update-non-oss/solv
/var/cache/zypp/solv/repo-update-non-oss/solv.idx
/var/cache/zypp/solv/repo-update-non-oss/cookie
/var/cache/zypp/raw/repo-non-oss/repodata/repomd.xml
/var/cache/zypp/raw/repo-oss/repodata/repomd.xml
/var/cache/zypp/raw/repo-update/repodata/repomd.xml.asc
/var/cache/zypp/raw/repo-update/repodata/repomd.xml.key
/var/cache/zypp/raw/repo-update/repodata/repomd.xml
/var/cache/zypp/raw/repo-update/repodata/273195586bbb062571dbfd52c38eb43a3a3803f4dc494d65727b05cda0f03484-deltainfo.xml.gz
/var/cache/zypp/raw/repo-update/repodata/f3a1b3c79aac6eaa3fa42d123154a930979b62ec1452b8a3ec7d19fcd7f9b7a9-primary.xml.gz
/var/cache/zypp/raw/repo-update/repodata/588446849db9957cd0f04a9a3b94567585eaddba0ee987ef832525e1f874b392-updateinfo.xml.gz
/var/cache/zypp/raw/repo-update-non-oss/repodata/repomd.xml.asc
/var/cache/zypp/raw/repo-update-non-oss/repodata/repomd.xml.key
/var/cache/zypp/raw/repo-update-non-oss/repodata/repomd.xml
/var/cache/zypp/raw/repo-update-non-oss/repodata/df83a5f32b6fe74beb5323e78c087c2fe42cc8d9dc8843c153a579d114bc65d8-deltainfo.xml.gz
/var/cache/zypp/raw/repo-update-non-oss/repodata/e441b6b08c7c2261701ca11fdbecec4e13f20e8e09b444d158d5b85a0da1e260-primary.xml.gz
/var/cache/zypp/raw/repo-update-non-oss/repodata/60b8499fd62600e4c2ddb31cefed60cb408b43376c04f1c0aa48736dd8cb27fd-updateinfo.xml.gz
/var/lib/YaST2/cookies
/var/lib/systemd/migrated/cron
/var/lib/zypp/LastDistributionFlavor
/var/lib/zypp/AutoInstalled
/var/log/journal/f172a8a449fc4435bfaac0127f2f8731/system@686b73ecd6c24329921f5897a04e5f25-00000000000006b3-0005c3b6f7edf213.journal
/var/log/zypp/history
/var/log/zypper.log
/var/log/vmware-vmsvc-root.log
/var/log/vmware-vgauthsvc.log.0
/var/log/vmware-network.3.log
/var/log/vmware-network.2.log
/var/log/vmware-network.1.log
/var/log/vmware-network.log
/var/spool/cron/tabs/root
/usr/bin/dot
/usr/lib/sysimage/rpm/Basenames
/usr/lib/sysimage/rpm/Conflictname
/usr/lib/sysimage/rpm/Dirnames
/usr/lib/sysimage/rpm/Group
/usr/lib/sysimage/rpm/Installtid
/usr/lib/sysimage/rpm/Name
/usr/lib/sysimage/rpm/Packages
/usr/lib/sysimage/rpm/Providename
/usr/lib/sysimage/rpm/Recommendname
/usr/lib/sysimage/rpm/Requirename
/usr/lib/sysimage/rpm/Sha1header
/usr/lib/sysimage/rpm/Sigmd5
/usr/lib/sysimage/rpm/Suggestname
/usr/lib/zyppe
/etc/sysconfig/cron
/etc/motd
/etc/Quijote.txt
To focus on ELF files,
|
|
/etc/motd and /etc/Quijote.txt may be helpful later.
Encryption binary
It turns out /usr/lib/zyppe was the encryption binary. Analyzing the binary in IDA, we find that the binary is relatively simple, with the main function finding all files within the HOME/Documents folder then encrypting the contents in 1024-byte blocks using the function encrypt, then writing the result to FILENAME.broken.
The encryption function uses a modified RC4 algorithm, with the key A secret is no longer a secret once someone knows it. The KSA remains the same, with the following pseudocode from IDA
|
|
However, the PRGA uses both the current and previous random character to encrypt the plaintext
|
|
We hence write a script to decrypt all the files.
|
|
Decrypted files
All the files that start with the same letter are somehow related.
Backberries
backberries.txt is a binary file of length 139
XORing with Reese's (from reeses.txt), we get
If you are not good in maths, the only thing that can save you is to be a bash expert. Otherwise you will be locked here forever HA HA HA!
Banana chips
banana_chips.txt is a binary file of length 140
XORing with Reese's (from reeses.txt), we get
Are you good at maths? We love maths at FLARE! We use this formula a lot to decode bytes: "ENCODED_BYTE + 27 + NUMBER1 * NUMBER2 - NUMBER3"
Recalling from .bash_profile that the numbers are 2, 3, and 37 respectively, we have some cipher ENCODED_BYTE + 27 + 2 * 3 - 37 = ENCODED_BYTE - 4.
Blue cheese
blue_cheese.txt is a binary file of length 38
XORing with Reese's (from reeses.txt), we get
The 4th byte of the password is: 0x35
Donuts
donuts.txt
Din moq agos etcp Ememog Lhobeihz Awttivt ytxtv drwvgoswps?
Doing a Bifid cipher with the keyword eggs, from nachos.txt, we get
Did you know that Giovan Battista Bellaso loved microwaves?
Giovan Battista Bellaso invented the Vinegere cipher.
Dumplings
dumplings.txt
Abn lef emadkxp frceqdnhe? Tah gdcktm temyku xxo qo ktyhzn! Zd'k raooua, por uda ztykqh.
Doing a Bifid cipher with the keyword eggs, from nachos.txt, we get
Are you missing something? You should search for it better! It's hidden, but not really.
Probably talking about .daiquiris.txt
Ice cream
ice_cream.txt
Mj$xlmw$gleppirki$mw$xss$hmjjmgypx$erh$}sy${erx$xs$kmzi$yt$sv$nywx$mr$gewi$}sy$ksx$lyrkv}0${lex$efsyx$feomrk$wsqi$qyjjmrwC$Xv}$xlmw$vigmti>.4$1$Gmrreqsr.5$1$Fyxxiv$594kv.6$1$Piqsr$536.7$1$Ikkw$7.8$1$Wykev$594kv.9$1$Jpsyv$694kv.:$1$Qmpo$74kv.;$1$Mgmrk$wykev$54kv.<$1$Ettpi$544kv.=$1$Vewtfivvmiw$544kv..Qm|$4$xs$=$erh$feoi$jsv$74$qmryxiw$ex$5<4ƴG2..
Using CyberChef’s SUB by 4 operation (from banana_chips.txt), we get this
If this challenge is too difficult and you want to give up or just in case you got hungry, what about baking some muffins? Try this recipe:
0 - Cinnamon
1 - Butter 150gr
2 - Lemon 1/2
3 - Eggs 3
4 - Sugar 150gr
5 - Flour 250gr
6 - Milk 30gr
7 - Icing sugar 10gr
8 - Apple 100gr
9 - Raspberries 100gr
Mix 0 to 9 and bake for 30 minutes at 180°C.
Iced coffee
iced_coffee.txt
Xli$srp}$tvsfpiq${mxl$VG8$mw$xlex$}sy$riih$e$oi}2$Xli$JPEVI$xieq$rsvqepp}$ywiw$xlmw$ryqfiv>$&WVIJFI&$,ew$er$YXJ1<$wxvmrk-2$Mj$}sy$lezi$rs$mhie${lex$xlex$qierw0$}sy$wlsyph$kmzi$yt$erh$feoi$wsqi$qyjjmrw2.
Using Cyberchef’s SUB by 4 operation (from banana_chips.txt), we get this
The only problem with RC4 is that you need a key. The FLARE team normally uses this number: "SREFBE" (as an UTF-8 string). If you have no idea what that means, you should give up and bake some muffins.*
As it turns out using that string as the RC4 key doesn’t work for any of the files. Since they said its a number and told us to refer to the muffin recipe which is in ice_cream.txt, we can guess that each letter corresponds to the instruction step number which has it as the first letter, so S is 4 because step 4 starts with “Sugar”. Hence this is telling us to use RC4 with the key 493513.
Instant noodles
instant_noodles.txt
Xli$9xl$f}xi$sj$xli$teww{svh$mw>$4|QW.
Using Cyberchef’s SUB by 4 operation (from banana_chips.txt), we get this
The 5th byte of the password is: 0xMS*
Here, using the same letter to number conversion from ice_cream.txt, we get 0x64.
Nachos
nachos.txt is some binary file of length 180
Using RC4 with the key 493513, which we get from iced_coffee.txt, we get
In the FLARE team we really like Felix Delastelle algorithms, specially the one which combines the Polybius square with transposition, and uses fractionation to achieve diffusion.
This is referring to the Bifid cipher, which Felix Delastelle invented.
Natillas
natillas.txt is some binary file of length 222
Using RC4 with the key 493513, which we get from iced_coffee.txt, we get
Do you know natillas? In Spain, this term refers to a custard dish made with milk and KEYWORD, similar to other European creams as crème anglaise. In Colombia, the delicacy does not include KEYWORD, and is called natilla.
This keyword obviously tells us which keyword to use with the Bipid cipher, and googling natillas, we find that the keyword referred to here is eggs.
Nutella
nutella.txt is some binary file of length 38
Using RC4 with the key 493513, which we get from iced_coffee.txt, we get
The 6th byte of the password is: 0x36
Oats
oats.txt
Kww jvkugh xatnfk phz JDMZG kswm dr Liqvksn. Tciq bwuk o xuigz an keharzwluvi jhqfa efp pcms crzel owpmsnsvxaav qe Hsioxwd!
pvkdo://trmlfmt.tci/aieeyi_06
jkhls://oaafbgi.qkm/HediitvAaccefuk
Doing Vigenere decoding with the key microwaves (which we get from oranges.txt) gives us
You should follow the FLARE team in Twitter. They post a bunch of interesting stuff and have great conversation on Twitter!
https://twitter.com/anamma_06
https://twitter.com/MalwareMechanic
Looking on Twitter, we see this thread which suggests AES with the key Sheep should sleep in a shed15.2, and the IV being @osardar1’s favorite food in caps, followed by 11 zeroes, meaning his favorite food is 5 letters. From his Twitter bio, we got FLARE RE, SW/FW/HW/PIZZA Dev, so the IV is PIZZA00000000000.
Omelettes
omelettes.txt
Kww jvkugh xatnfk phz JDMZG kswm dr Liqvksn. Oolwdekjs phzc emg ivh wnbvq mvf ecp lzx qac nvore zzwz qh pcq gzx ltm hcoc.
hoxhe://byzhpem.ggy/ipraia_06
cxlba://vnwptzv.uau/qjondvv1
zfbrj://hsioxwd.kqd/AwlrejqUgtvwndg
Doing Vigenere decoding with the key microwaves (which we get from oranges.txt) gives us
You should follow the FLARE team in Twitter. Otherwise they may get angry and not let you leave even if you get the flag.
https://twitter.com/anamma_06
https://twitter.com/osardar1
https://twitter.com/MalwareMechanic
Oranges
oranges.txt
Fpg 8kv xyoi gr bjv dwsnagdl kj: 0l60
Which clearly mean The 8th byte of the password is 0x60. It is probably a polyalphabetic cipher since trying Caesar cipher with all 26 keys doesn’t produce that message. We try to get a Vigenere cipher key to see if it makes sense by using the plaintext thethbyteofthepasswordis as the key which gets us the phrase microwaves, meaning this is Vigenere encrypted using that key.
The 8th byte of the password is: 0x60
Retrospectively, this could have been gotten from donuts.txt.
Raisins
raisins.txt is b64 encoded, giving
The 3rd byte of the password is.. it is a joke, we don't like raisins!
Rasberries
rasberries.txt is b64 encoded, giving
The 3rd byte of the password is: 0x51
Reeses
reeses.txt
V2UgTE9WRSAiUmVlc2UncyIsIHRoZXkgYXJlIGdyZWF0IGZvciBldmVyeXRoaW5nISBUaGV5IGFyZSBhbWF6aW5nIGluIGljZS1jcmVhbSBhbmQgdGhleSBldmVuIHdvcmsgYXMgYSBrZXkgZm9yIFhPUiBlbmNvZGluZy4K
Which b64 decodes to
We LOVE "Reese's", they are great for everything! They are amazing in ice-cream and they even work as a key for XOR encoding.
Shopping list
shopping_list.txt
/
[U]don noodles
[S]trawberries
[R]eese's
/
[B]anana chips
[I]ce Cream
[N]atillas
/
[D]onuts
[O]melettes
[T]acos
Sausages
When we do “rotate left” by 1 on sausages.txt, from ugali.txt, we get
The 2st byte of the password is 0x34
Spaghetti
When we do “rotate left” by 1 on spaghetti.txt, from ugali.txt, we get
In the FLARE language "spaghetti" is "c3BhZ2hldHRp".
Strawberries
strawberries.txt is itself a binary file, but rotating left by 1, from ugali.txt, we get
In the FLARE team we like to speak in code. You should learn our language, otherwise you want be able to speak with us when you escape (if you manage to escape!). For example, instead of "strawberries" we say "c3RyYXdiZXJyaWVz".
Base64 decoding c3RyYXdiZXJyaWVz just gives us strawberries.
Tacos
tacos.txt
27420b6486cfe04e872b09e3bddaa76ef575e5ef36e8306db062e2febc6d6cab46b4a761b2c0c3ce6f405c7add12ce0ec7483fb83876f0ceb20345d0597a4d995a188abb8793a3e433a19a7631dad4070715bc752cff0db74fbc7a06d97abbd7895559f4c2d3c86ef5433ee7b2738c3f512d18e101b904ff173296d03671b739beb783f37eecd39e7822e67c04e300b01a74a8e8f4d6b7edd21d5af52366fba06147431e9f46fb21bf6de2f005f70529
From oats.txt, converting hex to bytes and then running AES-CBC with they key Sheep should sleep in a shed15.2 and the IV PIZZA00000000000, we get
Woow! It seems you are very very close to get the flag! Be careful when converting decimal and hexadecimal values to ASCII and hurry up before we run out of tacos!
Tiramisu
tiramisu.txt
aa68c1adcfb5bcb550b4d2e44da48bb59b1cc86701cb3df2b2c81bc468e3c710b6e6a07c1bce4a04b2a34192823aa0b64f883783170f6c21d00b20c4a44c6acfdc2c8ab757bee984ac75dabd0e3f2bc9c215adb2d7db63e018e8d6cf1738e577d3da898d5ee8eb3276e51cf035146af8b558e5fa91ed2ee98e6795a7317569fcf77eb1cb679ae54c7b06db795ecd6c3a23862043a8938cf2733ab3ebd771e59dbde60e677c40491e1ccab3e792097d2f13389646ace071ed0494387506a077d5f4c0901793003dd8b3038f445305ea363006e7668913804b89e17dcef2fb4b3d96e77a444bdfacf82263f451ed4ddd79f38cf3b317ba759bec5405876723dcf4e08786deacd6ad34c97889f8c588263602a534f1e94b356d37e0d853ae50da18ef2752e105d1fd98697a72172c1c672b2e652290b558a3d20ae21d85f048444acf77c51e8c942aef341937227e517e7bac3c6710c5613a45f5767d675b856ebabe9f95115f1932e479e4fda350f7b8f621df84073672544080b70ca5607fd89e32691c2d06fee5354a23ecd156ccda9f0940bef01ded4d55ca7342016425b5ba00dee06d1f26307ea8fc4667a6772ddc
From oats.txt, converting hex to bytes and then running AES-CBC with they key Sheep should sleep in a shed15.2 and the IV PIZZA00000000000, we get
The 9th byte of the password is the atomic number of the element moscovium
The 10th byte of the password is the bell number preceding 203
The 12th byte of the password is the largest known number to be the sum of two primes in exactly two different ways
The 14th (and last byte) of the password is the sum of the number of participants from Spain, Singapore and Indonesia that finished the FLARE-ON 7, FLARE-ON 6 or FLARE-ON 5
For 9, the atomic number of Moscovium is 115, or 0x73
For 10, the bell number before 203 is 52 or 0x34
For 12, the largest known number to be the sum of two primes in exactly two different ways is 68, or 0x44
For 14, Flare-On 5 had 4, 6, 1 finishers, Flare-On 6 had 7, 25, 2 finishers, and Flare-On 7 had 9, 19, 0 finishers from the 3 countries, making a total of 72 or 0x49 (initially thought to be 0x48)
Tomatoes
tomatoes.txt
4892fbcc38c4a6aeeb2435081ec6cd83535b7f4e1ded18ad2a1ba9d5c5f825a6e53b343b0a04d39bf4c1fde228d0d958abea262bc8b4e5ac8eda08908be43e0354cf0bd78a3bbc23149776da6fdb4d4118f8095540113a2719e41308305727ac02831d3018e853d96b0f9d22e2866bff32b5565e2510e5dc25ac0b605fc929767d17f346c091cf91cd28c3ab0efa13b528aae1a7c2239e0348da44e0b814a80b8fded988f9bf3d1aee36ef42597767a41d2adb8ad7464cd5f248391665fc3dee05f0174bb0e5e8b5b3c26e021212e60a3f6462bcd04eba4a37ad2e76a07fdad2a00f02f7c4ac6cb825e5a98be1e6390b1d3bf481e1f79fb1ecf6a5dfce1e9615db51e51de7a48832a6bec04c3756b0b8
From oats.txt, converting hex to bytes and then running AES-CBC with they key Sheep should sleep in a shed15.2 and the IV PIZZA00000000000, we get
It seems you are close to escape... We are preparing the tomatoes to throw at you when you open the door! It is only a joke...
The 11th byte of the password is the number of unique words in /etc/Quijote.txt
The 13th byte of the password is revealed by the FLARE alias
For 11, we can just put the file into some online tool to get 108, or 0x6C
Udon noodles
udon_noodles.txt
"ugali", "unagi" and "udon noodles" are delicious. What a coincidence that all of them start by "u"!
Ugali
ugali.txt
Ugali with Sausages or Spaghetti is tasty. It doesn’t matter if you rotate it left or right, it is still tasty! You should try to come up with a great recipe using CyberChef.
The two files mentioned are non-ascii binary files.
Unagi
unagi.txt
The 1st byte of the password is 0x45
Daiquiris
.daiquiris.txt
|
|
This clearly says The 7th byte of the password is 0x66, but Caesar cipher and Vigenere cipher both don’t seem to work (Vigenere with the key xtyflgewajljrleyxfxqaipqp technically works but it doesn’t make a lot of sense).
Doing a Bifid cipher with the keyword eggs, from nachos.txt, we get
The 7th byte of the password is: 0x66
Checking the dot binary
shopping_list.txt told us to check /usr/bin/dot.
This file is an ELF binary that asks us for a password, then checks if the SHA256 hash is b3c20caa9a1a82add9503e0eac43f741793d2031eb1c6e830274ed5ea36238bf. If the password hash matches, it prints the flag.
Password
- 0x45 (
unagi.txt) - 0x34 (
sausages.txt) - 0x51 (
rasberries.txt) - 0x35 (
blue_cheese.txt) - 0x64 (
instant_noodles.txt) - 0x36 (
nutella.txt) - 0x66 ? (
.daiquiris.txt) - 0x60 (
oranges.txt) - 0x73 (
tiramisu.txt) - 0x34 (
tiramisu.txt) - 0x6C ? (
tomatoes.txt), originally thought 0x70 - 0x44 (
tiramisu.txt) - 0x35 (
.bashrc) - 0x49 ? (
tiramisu.txt), originally thought 0x48
We weren’t too sure about bytes 7, 11, and 14, and our initial values of 0x66, 0x70, and 0x48 didn’t give us the desired sha256 hash b3c20c..., so we wrote a script to brute force those 3 bytes
|
|
which gave us
$ python3 brute-force.py
b'E4Q5d6f`s4lD5I'
Flag
To get the flag, we just give our password to the dot file.
$ ./dot
Password: E4Q5d6f`s4lD5I
Correct password!
Flag: H4Ck3r_e5c4P3D@flare-on.com